Malvertising (the nefarious practice of placing digital ads leading to malware) has been making a resurgence over the past few weeks. For quite a while, cybercriminal gangs have been making fake websites leading to downloads of well-known software that is actually malware in disguise. This latest batch of malvertising, however, is coming from familiar faces on the darkweb (very familiar, in the case of Vermux and Google). When a mis-clicked link is the nightmare of security teams without powerful DNS filtering, it’s an issue worth watching. Here is our review of the most recent rounds of malware advertising that has been plaguing defenders and IT teams.
Cybercrime has an ad budget
In mid-December of 2022, several reports warned of Google Ads leading to websites laced with IcedID malware, commonly used in phishing attempts but newly surfacing in advertising campaigns. SANS began warning of Google Ads leading to fake software: the SANS research team found a Google ad showing a legitimate AnyDesk URL…but leading to a fake site after being clicked. These malvertising campaigns were used as a distribution technique for pushing IcedID malware (also known as Bokbot):
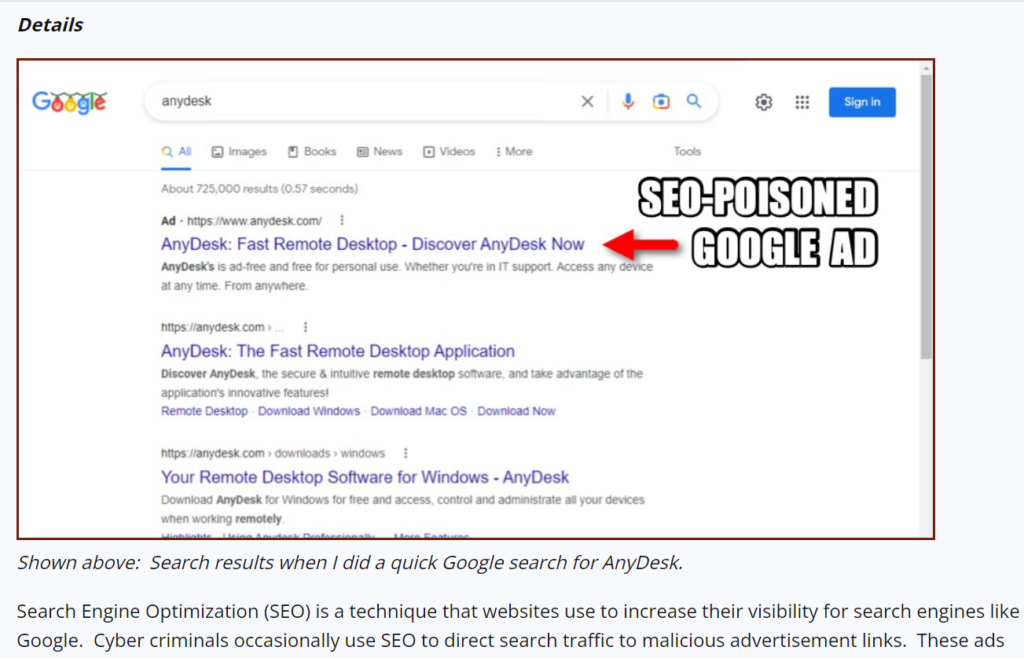
#image_title
Bencrypted identified the infection chain and then Colin Cowie shared more AnyDesk-specific data:
- Google search for “anydesk”
- Malicious ad click
- Redirect 1: getherkae[.]online
- Redirect 2: www-wwwanydesk[.]top/en/downloads/windows/
- Download: Setup_Win_14-12-2022_16-49-39.zip
- https://www.virustotal.com/gui/file/7cd30d
The following week, the FBI warned of search engine ads pushing malware and phishing to unsuspecting surfers around the globe. In this case, search engine advertisements have been promoting websites distributing ransomware or stealing login credentials for financial institutions and crypto exchanges. According to the federal law enforcement agency, threat actors purchase advertisements that impersonate legitimate businesses or services. As mentioned, these ads appear at the top of search result pages and link to sites that look identical to the impersonated company’s website. Most interesting, however, is the precise audience targeting the cybercriminals are using: it looks like the cybercriminals are targeting a certain kind of geek in the United States…
Malvertising meets Vermux
Guardio Labs then picked up the baton in malvertising research during the last week of December 2022, reporting Vermux malware (whose payload is mostly built based on the Vidar trojan) was behind many of the “masquerads” sites and domains the FBI originally referenced. The ads in this case have been served from Russia to target United States residents’ GPUs and crypto wallets:
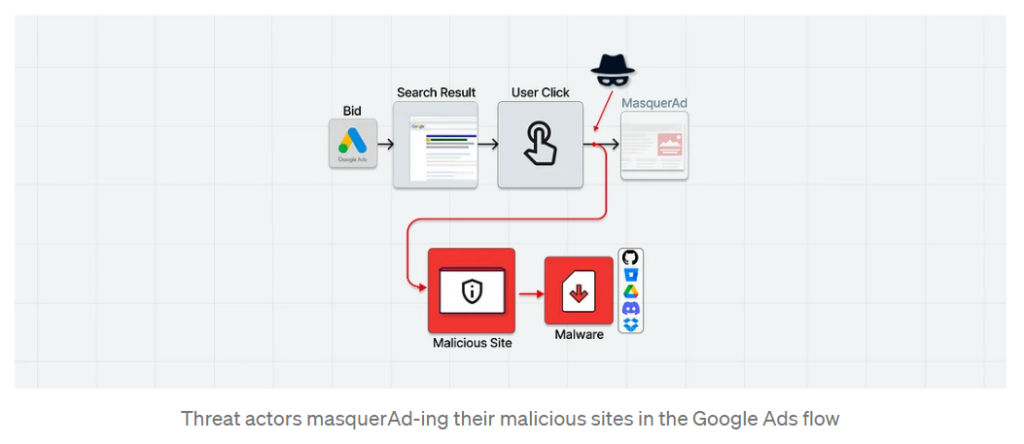
#image_title
Originally targeting searches for AnyDesk and MSI Afterburner to proliferate cryptocurrency miners and Vidar information stealer, “those rogue sites are practically invisible to visitors not reaching from the real promotional flow (e.g., arriving with a valid gclid value) showing up as benign, unrelated sites to crawlers, bots, occasional visitors, and of course for Google’s policy enforcers,” reports the research team. Peek below for examples of the promotional flows, active during December 2022.
On the left is the masked site Google is actually advertising, while on the right is the maliciously advertised phishing site:

#image_title
Of particular interest is the gang’s choice to target Brave downloads, too, delivering the payload directly into the hands of the security-minded surfers of the internet.
How are Vidar and Vermux related?
The Vidar stealer that forms the backbone of Vermux was popularized by the threat actors behind GandGrab; Vidar stealer is a fork of the Arkei stealer according to threat researcher Fumik0. It has some of the classic features of stealers:
- Searching for specific documents
- Stealing ID from cookie browsers
- Stealing browser histories (also from the Tor Browser)
- Stealing wallets
- Stealing data from 2FA software
- Grabbing messages from messenger software
- Screenshot
- Loader settings
- Telegram notifications (on server-side)
- Getting a complete snapshot of all information of the computer victim
As part of this group of campaigns, the Vermux researchers also uncovered Gramnarly malware – which is a racoon stealer variant with bloated files that changes payloads periodically, making it even more evasive to detect.
Don’t forget about typosquatting
Malvertising also encompasses typosquatting, also resurging in late 2022: BleepingComputer recently helped reveal a massive typosquatting campaign using over 200 websites impersonating software projects, cryptocurrency exchanges, and wallet platforms to push Windows and Android malware. They recently uncovered a vast network of fake sites pretending to be Google Play, TikTok, and PayPal download portals. A snapshot of some of the domains:
snanpckat-apk[.]com – impersonates Snapchat
vidmates-app[.]com – impersonates VidMate
paltpal-apk[.]com – impersonates PayPal
m-apkpures[.]com – impersonates APKPure
tlktok-apk[.]link – impersonates download portal for TikTok app
In all cases, when the user attempts a download the APKs, they get ERMAC instead: a banking trojan targeting banking accounts and cryptocurrency wallets from 467 apps.
As part of their research, the same BleepingComputer team then found an even bigger typosquatting campaign from the same malware merchants – but this time specializing in distributing Windows malware, which is particularly devastating for enterprise infrastructure. This campaign spans 90 websites that were created to impersonate over twenty-seven popular brands including Microsoft Visual Studio, PayPal, and TikTok. The sites distribute Windows malware, steal cryptocurrency recovery keys, as well as pushing Android malware.
Malware continues to iterate version after version of itself and its guerrilla distribution network rivals that of any formal supply chain. But their distribution is effective and will continue to innovate, which means good tools innovate at the same pace. Ransomware and data exfiltration are outcomes of poor security; a robust security solution that includes DNS filtering will prevent most users from clicking on bad links from malvertising in the first place, thus protecting your users, applications, and resources.
Stay ahead of the latest issues affecting your security posture with the Banyan blog.
*Researched and authored by Mademoiselle



