If it were an arm-wrestling match, it’s possible that Secure Access Service Edge (SASE) would beat Security Service Edge (SSE) if measured by bulk force alone. But if you’ve ever watched arm-wrestling (or any kind of wrestling), sometimes power and agility count for more than size and weight. In fact, in the last quarter of 2022, SSEs represented nearly 60 percent of the SASE market by revenue. The remainder, 40 percent, was SD-WAN…so it’s absolutely worth paying attention to that smaller, more agile player right now. While the secure access service edge and the security service edge definitely have overlap, they are suited to solve slightly different problems for the enterprise. Let’s take a look at which one you might need and when.
Where did the Secure Access Service Edge come from?
In 2019, Gartner recognized a new market segment for SASE and gave it a label: SASE is a network security architecture grouping SD-WAN, SWG, CASB, ZTNA and FWaaS as core abilities. SASE combines network security services with wide-area network (WAN) capabilities (like the SD-WAN software-defined wide-area networking mentioned above). SASE delivers network and security services from the cloud and aims to provide secure access to any application, regardless of where it is hosted.
SASE creates regionally distributed points of presence (PoPs) using a software-based virtual network; the PoPs provide nearby secure networking and cloud-based security functions to both branch offices and remote users. Bringing secure networking geographically closer to its users, SASE reduces lag and latency, vanishes the need for perimeter edge and security appliances like routers and firewalls, archives the obsolete perimeter model, and lets organizations shift from on-prem to cloud-based security and internetworking solutions.
To simplify: SASE uses a software-based virtual network to create regionally distributed points of presence (PoPs) that provide nearby secure networking and cloud-based security functions to branch offices and remote users. SASE brings security and networking geographically closer to users, cuts down lag and latency, eliminates the need for a company VPN, abolishes the obsolete perimeter model and lets organizations shift from on-premises to cloud-based security solutions. Rather than relying on the security of the data center, traffic from users’ devices gets inspected at a nearby PoP (the enforcement point) and sent onward from there.
SASE has several components:
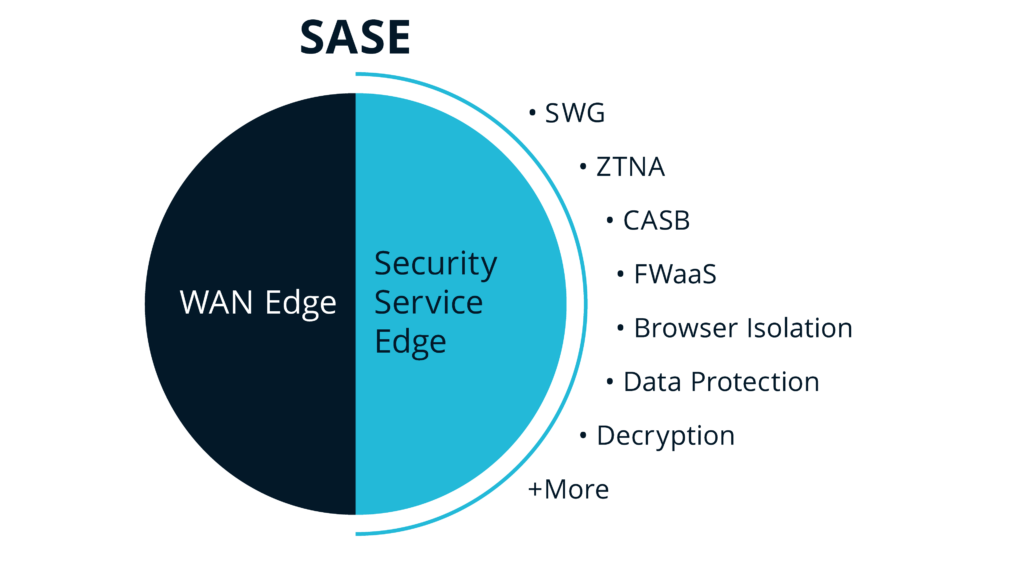
- CASB – Cloud access security brokers control traffic between the employees and company cloud instances and web applications. CASB can include access monitoring (IAM), endpoint detection and response (EDR) and data loss prevention (DLP).
- FWaaS – Cloud-based firewall-as-a-service filters network traffic according to the organization’s rules; can include next-gen (NGFW) functions like intrusion prevention/detection (IPS/IDS) or domain-name-system (DNS) security.
- SD-WAN – Software-defined wide-area networks securely link branch offices, data centers and remote users. The SD-WAN may overlay the public internet, may use a private backbone to link to PoPs—or both.
- SWG – Secure web gateways monitor, inspect and log users’ web traffic as well as blocking intrusions and malware. It can also filter content and block specific URLs according to organizational policy.
- ZTNA – Zero-trust network access verifies and authenticates each user upon access, regardless of user location. You can restrict lateral network movement with additional authorization requirements.
- Browser Isolation – protects users from untrusted, potentially malicious websites and apps by confining browsing activity to a secured environment that is separate from devices and networks.
- Data Protection – protecting sensitive information from damage, loss, or corruption.
And here comes SSE…
Two years after the initial SASE marketization, the team noticed another shift in corporate usage (namely, that many organizations weren’t adopting the SASE model). This trend led to Gartner defining SSE in 2021 as “securing service edge access to the web, cloud services and private applications…includ[ing] access control, threat protection, data security, security monitoring, and acceptable-use control enforced by network-based and API-based integration.”
SSE is SASE without the bulk of the SD-WAN, but still retaining the CASB, SWG, VPNaaS, and ZTNA functions: PoPs can be connected over the internet and enforced using the zero-trust policies instead of the SD-WAN. Many cloud-based companies simply don’t need SASE as SD-WAN is ideally suited for companies with both branch offices and remote workers.
What makes up the Security Service Edge
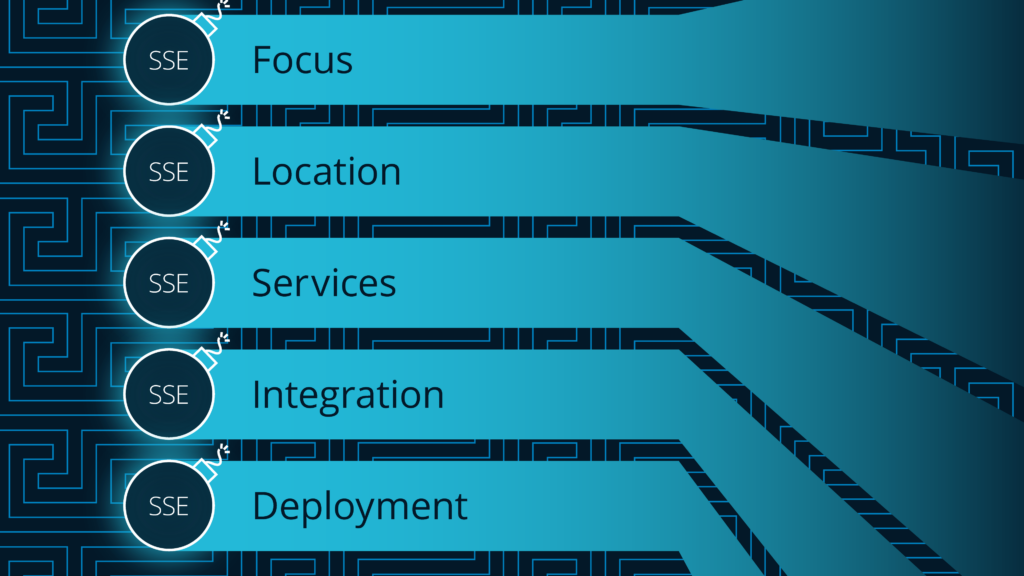
Focus: SSE primarily focuses on delivering security services for all traffic and resource access, while SASE is designed to provide edge networking, interconnectivity between all sites, and network security services to users accessing applications from anywhere in the world.
Location: SSE delivers security services at the edge of the network, which is typically the branch office or endpoint. SASE delivers connectivity and security services using a multi-tenant cloud.
Services: SSE provides a comprehensive set of security services, including ZTNA, VPNaaS, CASB, and SWG. SASE services include edge networking functionality such as FWaaS and SD-WAN, along with some less-frequently-used functionality such as remote browser isolation.
Integration: SSE is typically integrated with other security technologies, such as endpoint detection and response (EDR) and security information and event management (SIEM) systems. SASE is designed to be its own unified platform that provides multiple security and networking services, which often results in vendor lock-in.
Deployment: SSE is deployed more quickly (with the right product) and can overlay on top of existing edge and cloud networking products, while a SASE deployment may require multiple components (and a complete re-architecting of networks). SASE may also be deployed alongside other security platforms, assuming investment around integrating the tools.
A respondent to a 2022 Cyber Risk Alliance survey on cloud security said “my organization is most likely to consider purchasing an [SSE] solution that is a one-platform, comprehensive network security solution,” because this approach is more efficient and cost-effective than purchasing individual solutions for each aspect of network security. That sentiment seems to be reverberating throughout the industry, when 60% of companies recently chose SSE instead of SASE.



