Banyan Security is now
part of SonicWall
SonicWall acquires Banyan Security, accelerating its SASE offerings.
Jumpstart your journey to a
device-centric Security Service Edge (SSE)


Connect to your network over the internet using a secure, encrypted tunnel.

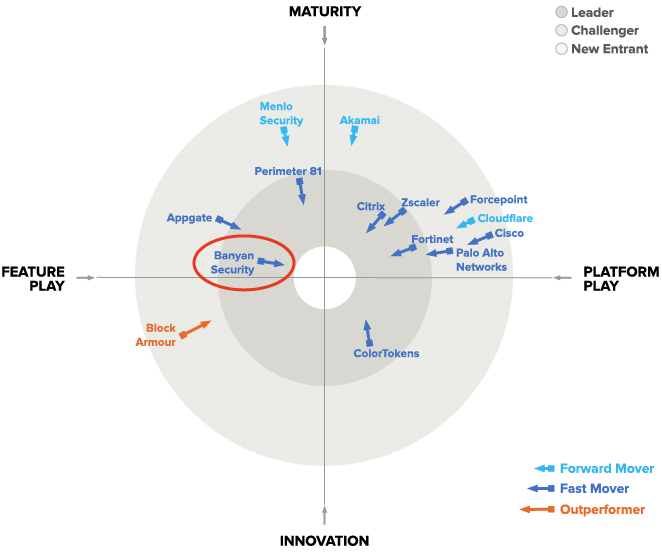
Banyan Security is Named a ZTNA Market Leader
See why Banyan Security is named a market leader through insights provided by GigaOm analysis in this just-released report.
Secure application, infrastructure, and network access, purpose-built for enterprises
Banyan replaces your traditional security appliances – VPNs, bastion hosts, proxies, and gateways – with a cloud-based zero trust access solution. Easy. Fast. Secure.
Networking 
Dead simple setup. High-performance connectivity. Learn More →
Security 
Transform enterprise security. Granular policy controls. Learn More →
DevOps 
One-click infra access. Never expose private networks. Learn More →

Modernize Enterprise Networking
Dead-simple setup. Reduced network complexity. High-performance connectivity.
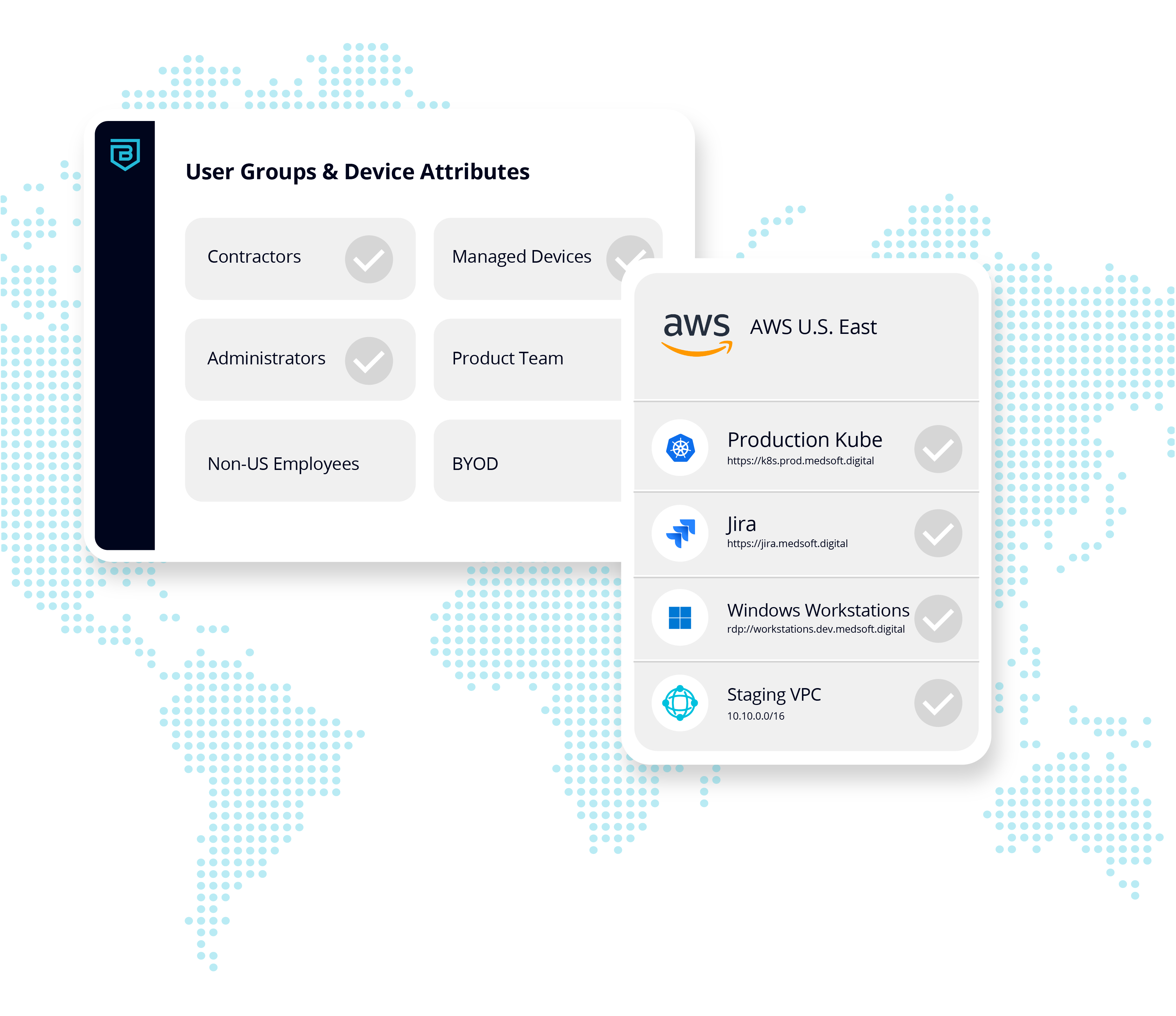
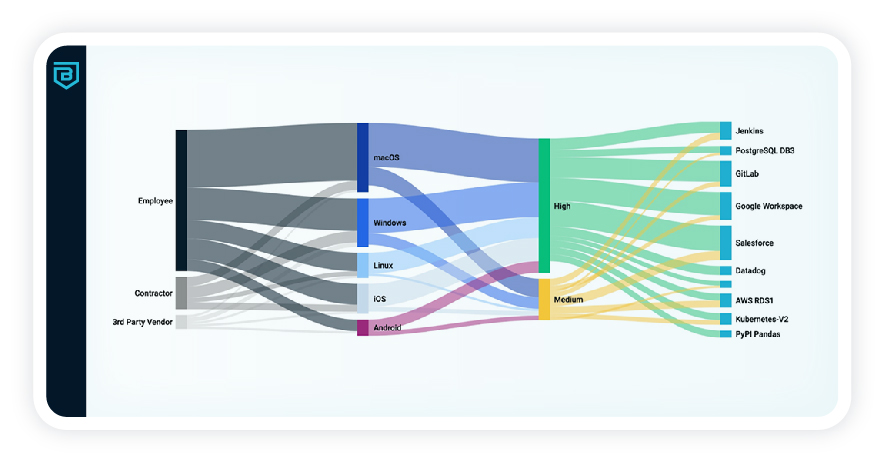
Transform Workforce Security
Granular zero trust policy controls ensure only the right users and devices see and access resources.
Automated One-Click Services Access
Easy access to critical on-premises and cloud services, without exposing private networks.

Lemonade Insurance secures remote employees with Banyan

“The increased security we get with Banyan is tremendous. Compared to our VPN it’s night and day.”
Jonathan Jaffe Lemonade CISO
- Onboard new users with access to the right resources
- Improve security with device trust
- Increase employee productivity and end-user satisfaction
Start now for free