Establishing Device Trust
Users and their devices are the weak link in most organizations’ security chain. Banyan Security's Device Trust ensures end users only access applications, data, and services from known trusted devices.Banyan Device Trust
Today, most access decisions are made on the basis of simple user authentication, failing to factor in device identity and posture, putting sensitive applications, data, and services at risk. The diverse population of employees, developers, temporary workers, and third parties means you can’t afford to implicitly trust the devices they are using.
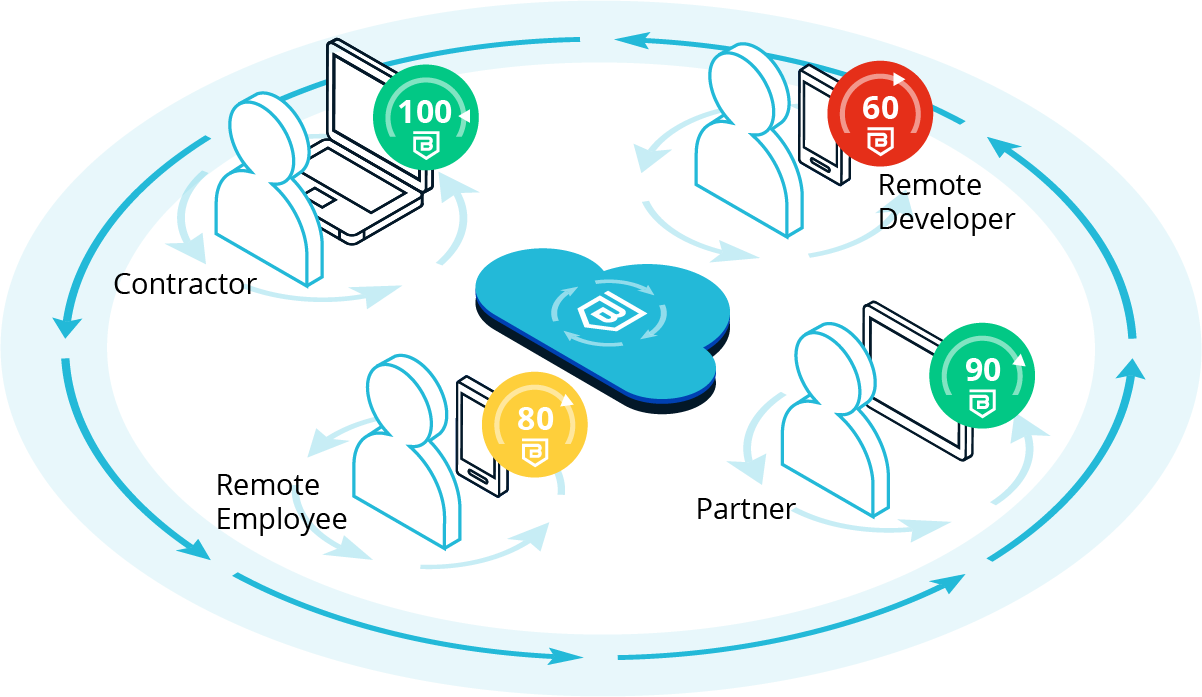
Banyan makes it easy to achieve real-time device trust, a critical component for comprehensive zero trust access.
The Obstacles

So Many Devices and Uses
- No single device management solution provides complete coverage across all popular operating systems (Windows, macOS, iOS, Android, Linux).
- Contractors, temporary workers, and third parties are usually unwilling or unable to use an organization’s heavy-handed device management systems (MDM, UEM, etc.).
Device Security
- User authentication and MFA systems do not register and authorize devices. Device Trust is a critical component of Zero Trust.
- There is no way to continuously know the security status of a device. Checks done only at the time of initial login are not effective when work happens 24x7x365.

Cost and Enforcement
- Device management silos and EDR do not integrate with access policy enforcement across users, devices, and resources.
- End-user frustration with multiple VPN and VDI clients and their complex security requirements hurts productivity.
Getting Started with Device Trust
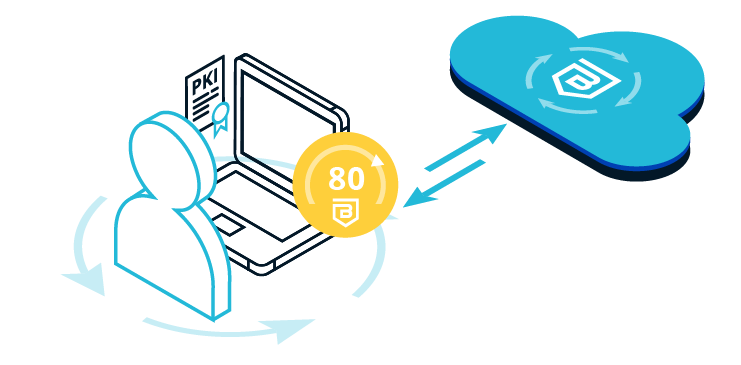
Device trust requires certified unique identification of the user’s device and real-time assessment of its risk posture.
Using Device Trust for Continuous Access Authorization
- Create Access Policy against context of user identity, device trust, and resource sensitivity in the cloud admin console.
- Lightweight App Installation initiated by the user or via a silent install supports all device types.
- Device Authorization uniquely registers all devices, regardless of platform type or device management software on the system.
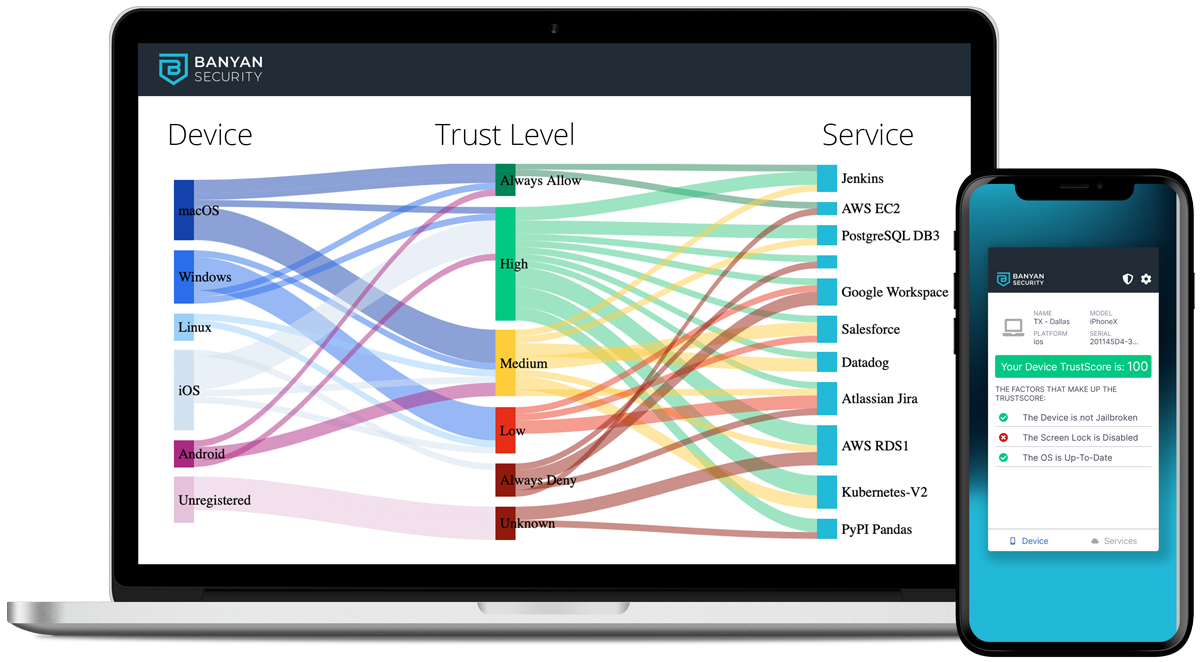
- Banyan Trust Level is immediately visible upon application installation enabling users to self-remediate if their devices do not meet the security posture requirements for a requested resource.
- Continuous Re-Authorization of device trust enforces access policy requirements, immediately disconnecting when a user’s device is no longer compliant.
Banyan Device Trust Benefits

Security Clarity
- Allow only known, verified devices (managed / unmanaged / BYOD) into your network to access resources.
- Enable device trust security controls for resource, IaaS, and SaaS application access.

Set-Up Simplicity
- Download the lightweight Banyan app, and manage policies from a cloud-based platform.
- Transparently integrate with existing SSO, MDM, and EDR tools without needing additional setup.
Manageability
- Achieve granular trust-based policy control and visibility across all devices connecting to your organization.
- Continuous audit logs of who and which device accessed what resources and when. Easily stream data into your SIEM or security framework.
Key Features for Device Trust
- Real-time verification of user and device trust before granting access using employee-visible Banyan TrustScore.
- Passwordless access using device certificates ensures only trusted devices can access resources and applications.
- Respond to device loss and theft by invalidating its certificate. Active sessions are dropped, and future access to resources, IaaS, and SaaS applications is blocked.
