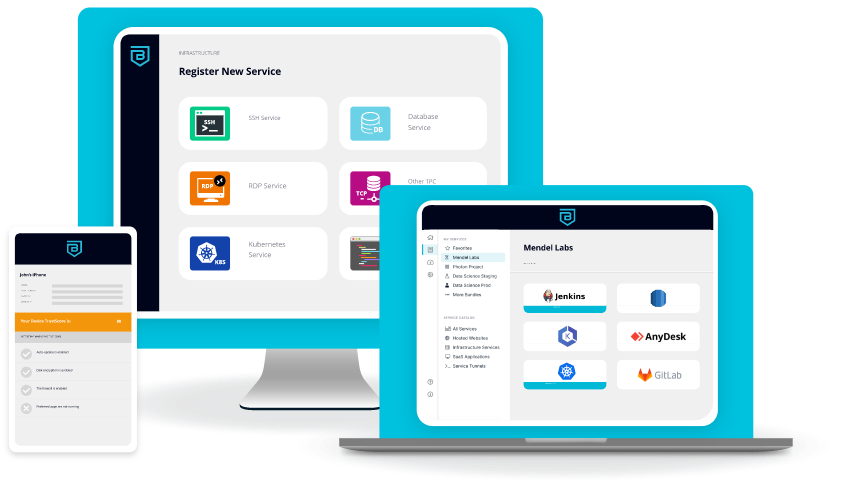
Banyan Security Platform
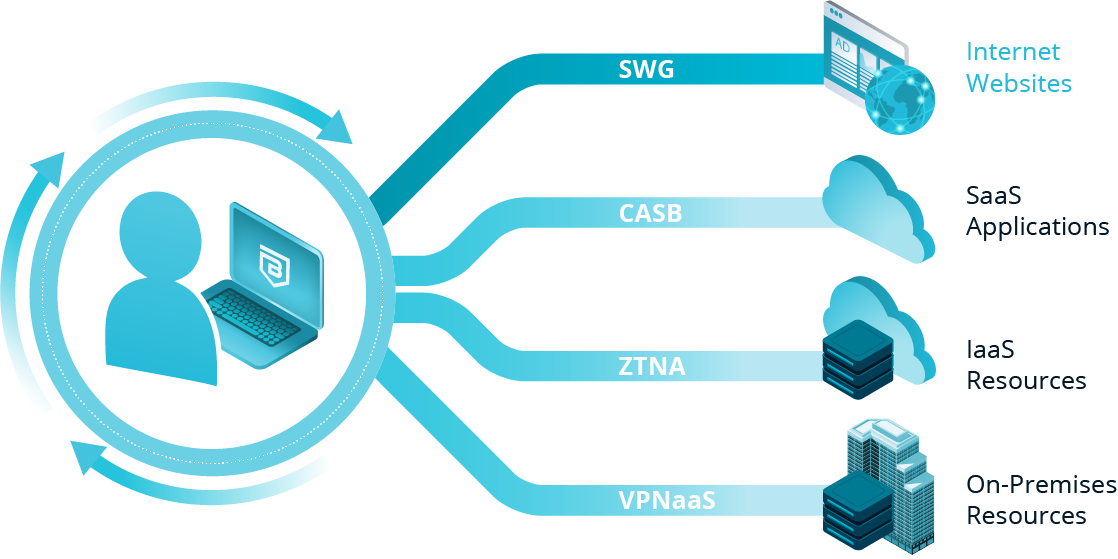
Providing secure access to websites, SaaS applications, private applications, and infrastructure while protecting organizations from internet threats.
Device-Centric Security Service Edge (SSE) Simply Makes Sense
Device-Centric SSE Benefits
Device-centric SSE is revolutionary, providing organizations with considerable benefits including:

User Experience
- Superior performance vs. cloud-centric solutions
- Low latency, always-on, not always inline security delights users

Security
- Continuous authorization driven by advanced user/device/resource risk modeling
- Existing security telemetry (e.g., EDR) factored into real-time evaluation

Data Privacy
- Traffic not inspected in vendor cloud
- Flexible Edge provides full control of data plane

Simplicity and Cost
- Easier to deploy, manage, and use
- Lower bandwidth consumption
- Fewer helpdesk tickets
- Faster onboarding / offboarding
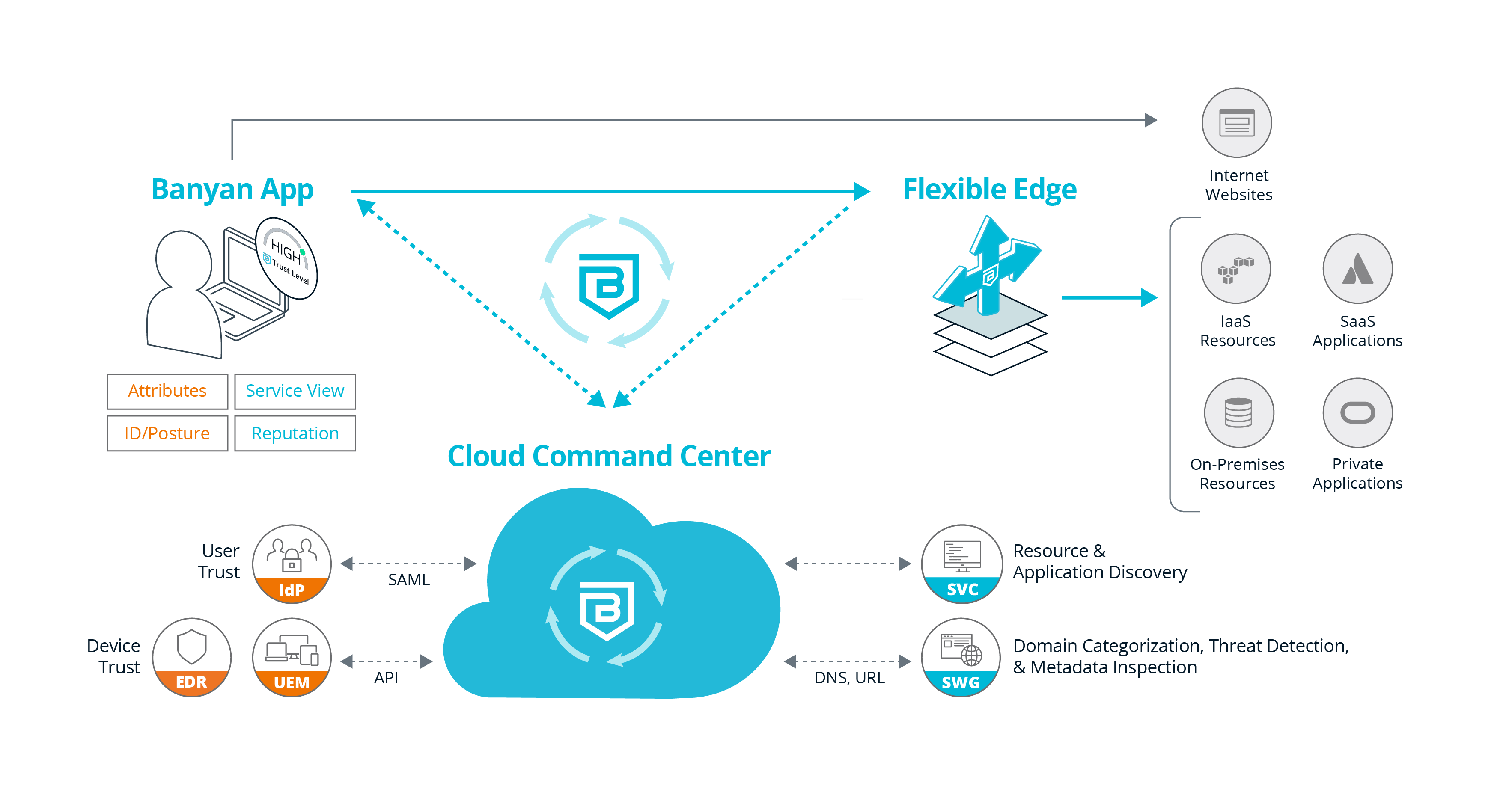
Banyan Architecture
Built as a cloud-based solution from the ground up, the Banyan Security Platform delivers ground-breaking device-centric Security Service Edge (SSE) capabilities for today’s modern workforce. Applications and resources must be securely accessible on-premises and remote, and in SaaS, IaaS, and internet environments. And most of all, we’ve made it easy to make progress toward your zero trust vision.
Still Have Questions?
We have compiled a list of frequently asked questions and their answers to help you fully understand our product, and more importantly our approach, to securing access to all of your valuable corporate assets and services.
Read the FAQ →
Integrations
Your Technology Investments Can Do More
With our extensible pre-built integrations and framework, we can easily connect with your existing cloud, IAM, MDM, EDR, and UEBA tools. Explore how Banyan Security can help you leverage your existing investments to gain a zero trust security posture today.