NETWORKING
Dead-Simple Deployment, Setup, and Management

Deploy incrementally, in minutes, alongside your existing infrastructure
Tenant creation to first end user login can be done in minutes
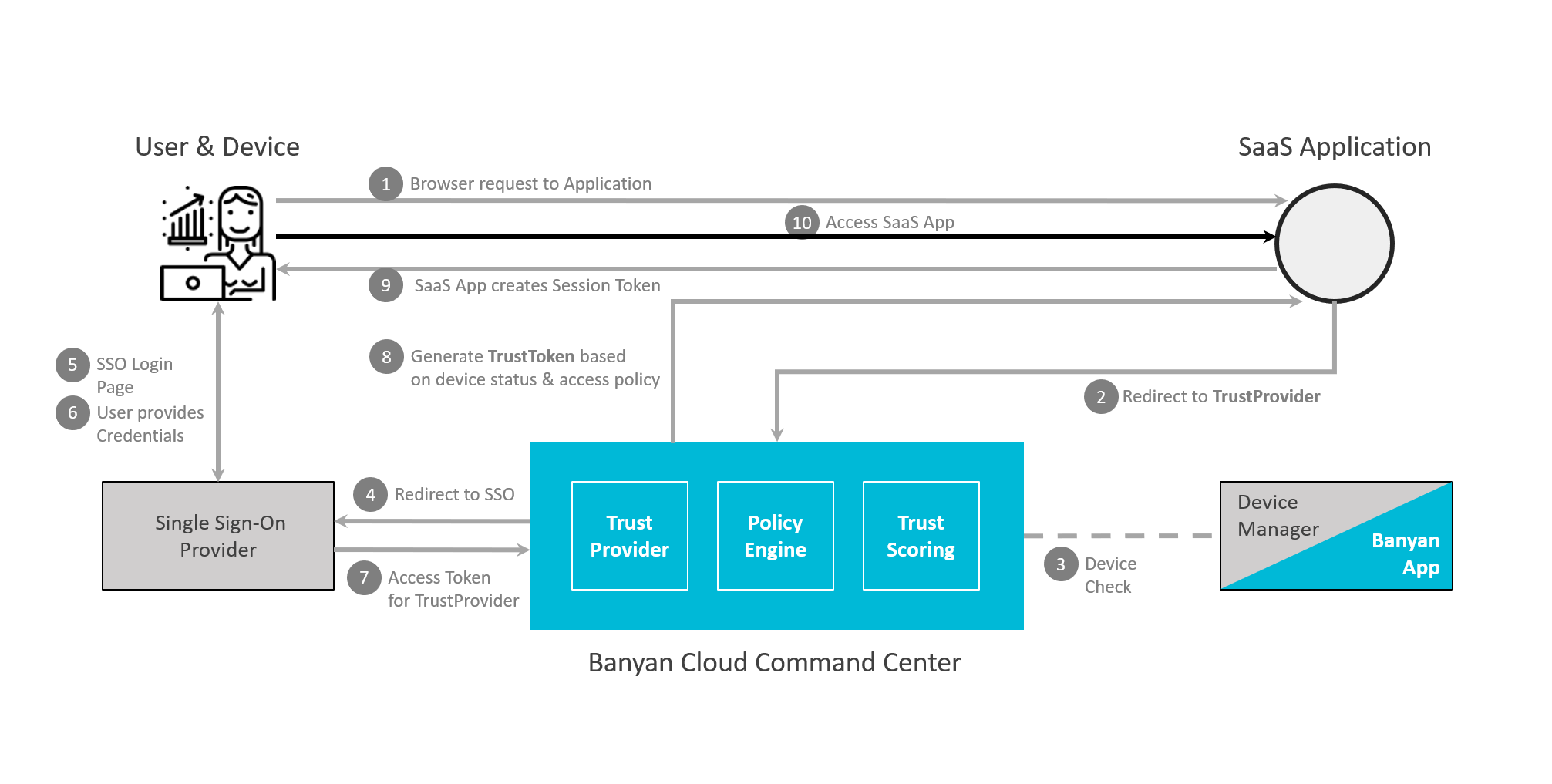
Most components are hosted by Banyan and are already up and running. Banyan’s Global Edge deployment features a SaaS-based Controller that’s always running and up-to-date. Nothing to deploy other than a lightweight connector that deploys in minutes.
Global Edge uses cloud-based data planes deployed by Banyan and only requires the deployment of a lightweight connector.
- This method can be deployed in minutes as no changes to edge devices are needed.
- The connector runs on all flavors of Linux which means it can really run anywhere including all CSPs, hypervisors, Raspberry Pis, and the Windows Subsystem for Linux (WSL).
The Banyan desktop app is available from https://www.getbanyan.app/download/ and the mobile app is available from the Apple App Store and Google Play. For desktop, there are multiple ways to deploy including a Zero Touch Deployment method using MDM/UEM.
Integrate with existing identity providers using SAML and/or ODIC
Integrate with other security solutions using APIs
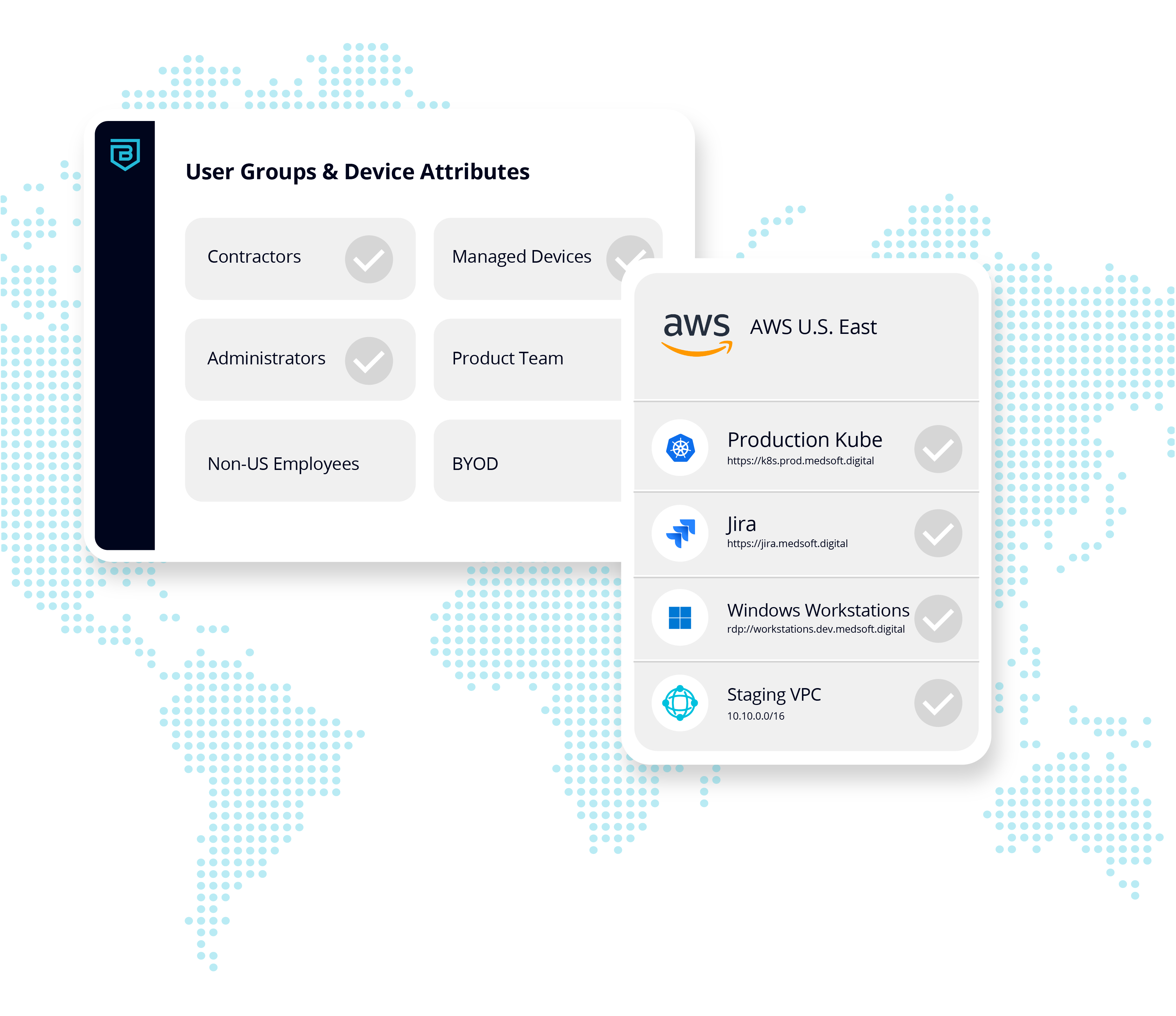
Simple user/device/resource-based policies instead of complex and fragile IP addresses, segments, etc. enable easy user-to-application segmentation.

Simplifying your network means not having to rely on various network devices to act as Policy Enforcement Points (PEPs).
Policy Enforcement is built into the Banyan components. This means that a flat network can be used with Banyan’s Private Edge Access Tier deployed. While the backend network is visible to Banyan, based on configured subnets, the backend resources are not visible or accessible to end users unless they are authenticated and authorized.
To further simplify the deployment for your IT team and improve the end user experience, using the same authentication and access methods regardless of end user location (remote or on-premises) is recommended. This simplifies end user training, ensuring a consistent user experience regardless of location. This may also result in not requiring a Network Access Control (NAC) solution when on-premises.
Securely and easily extend access to third parties, supporting BYOD with granular trust-based access control policies.
Create policies that allow for unregistered devices based on source IP addresses and subnets. This is useful for third parties that can’t or won’t install the Banyan app.
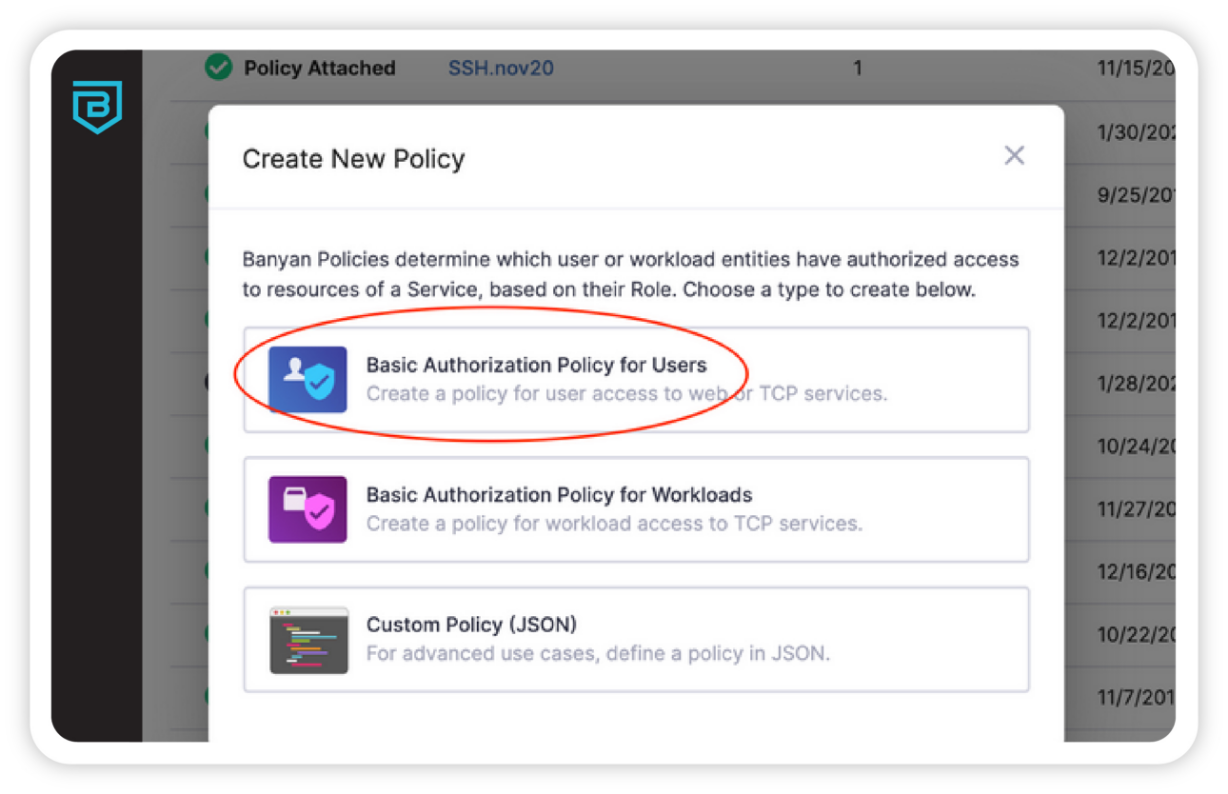
Single policy set whether on-premises or remote, private network, or cloud.
Create a single authentication and authorization policy regardless of where the user is located or where the resource lives.
This also enables you to add more authentication types and device posture assessment to SaaS applications that don’t natively support them.