Providing secure zero trust access and advanced internet threat protection for the modern workforce
A Security Service Edge (SSE) solution, the Banyan Security Platform securely connects users to applications, resources, and infrastructure while protecting them from internet threats. Risk and security are continuously evaluated, incorporating telemetry from existing security tools. In short, Banyan enables “Work From Anywhere” for the modern enterprise where users, regardless of location, can safely and securely access corporate and internet resources.
Legacy VPNs and firewalls reveal significant performance, manageability, and security limitations when trying to provide simple, safe, and secure access to the applications and resources users need across hybrid, multi-cloud, and SaaS environments. And, users are left open to attack accessing internet-based information and applications. To address these realities, a scalable and comprehensive approach to safe, secure access is required.
Banyan provides device-centric access to the applications, resources, and information your workforce needs.
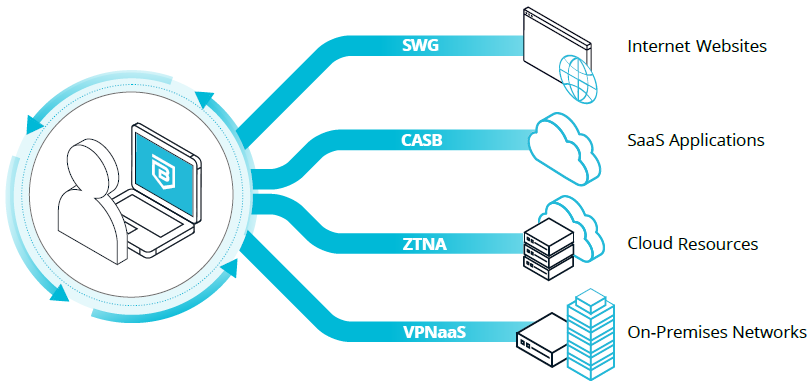
| Secure Web Gateway (SWG) Internet threat protection Guards against phishing, straying onto malicious web sites, and ransomware exposure. Organizations may also block specific categories of web sites, like gambling and pornography. |
Zero Trust Network Access (ZTNA) Application and infrastructure access Simple, least privilege access to applications and services across hybrid- and multi-cloud infrastructure, leveraging your existing enterprise identity and security tool investments. |
|
| Cloud Access Security Broker (CASB) SaaS application access security Layered security provides easily managed controls to enforce who, using what specific devices, can access your SaaS applications. |
Virtual Private Network as a Service (VPNaaS) Network access Modern, high-performance tunnel-based access to networks, incorporating zero trust enhancements like continuous authorization and device trust. |
Why Banyan
Zero Trust Use Cases
Modernize VPN & Firewall
Rather than rely on coarse tools like firewalls and legacy VPNs to protect company resources, enable least-privilege access to specific applications and servers based on the combined real-time contextual factors of user and device trust and resource sensitivity. Deploy incrementally – alongside existing infrastructure, if desired.
Support Third-Party Access / BYOD / M&A
Provide third-parties easy, secure access to only the specific resources they need, optionally incorporating device trust (below). Enable BYOD without needing Mobile Device Management (MDM) or Unified Endpoint Management (UEM). Corporate assets are continually protected while delivering an enhanced user experience that doesn’t require control of users’ preferred devices.
Device Trust & Internet Threat Protection
Device trust augments user trust, uniquely identifying devices and assessing their security posture. Granular policies enforce user and device identity, device posture, and resource sensitivity, reducing the risk of credential loss and theft. Protect workers from being phished, straying onto malicious web sites, or being exposed to ransomware. Additionally, domains can be blocked by category to ensure corporate compliance.
Zero Trust Use Cases
Modernize VPN & Firewall
Rather than rely on coarse tools like firewalls and legacy VPNs to protect company resources, enable least-privilege access to specific applications and servers based on the combined real-time contextual factors of user and device trust and resource sensitivity. Deploy incrementally – alongside existing infrastructure, if desired.
Support Third-Party Access / BYOD / M&A
Provide third-parties easy, secure access to only the specific resources they need, optionally incorporating device trust (below). Enable BYOD without needing Mobile Device Management (MDM) or Unified Endpoint Management (UEM). Corporate assets are continually protected while delivering an enhanced user experience that doesn’t require control of users’ preferred devices.
Device Trust & Internet Threat Protection
Device trust augments user trust, uniquely identifying devices and assessing their security posture. Granular policies enforce user and device identity, device posture, and resource sensitivity, reducing the risk of credential loss and theft. Protect workers from being phished, straying onto malicious web sites, or being exposed to ransomware. Additionally, domains can be blocked by category to ensure corporate compliance.