Elevate Third-Party & BYOD Access and Control – Create Trust Boundaries to Enhance Business Outcomes
Challenges continue to rise, and more organizations than ever are reliant on third parties to provide the resources, talent, and speed to deliver on their business goals and growth. Previous ways of granting access to needed resources and applications don’t fit today’s security and compliance needs. Achieve continuous adaptive security that checks against profile changes and system configurations, directly controlling third-party access into your organization’s resources.
Easily create global or granular policies with a clear understanding of what resources that a role, individual, or device can interact with so they will be productive without sacrificing organizational security. No need for complex VPNs, network segmentations, or firewall exceptions that have limited documentation. Forgo managing the whitelisting of IP addresses. Elevate third-party and BYOD access and control by setting specifications for access that incorporate real-time contextual security information on the user, device, and requested resource. Set policies that are just right for your business needs, defining access assignment by network, cloud service, application, URL, and even individual API-level permissions.
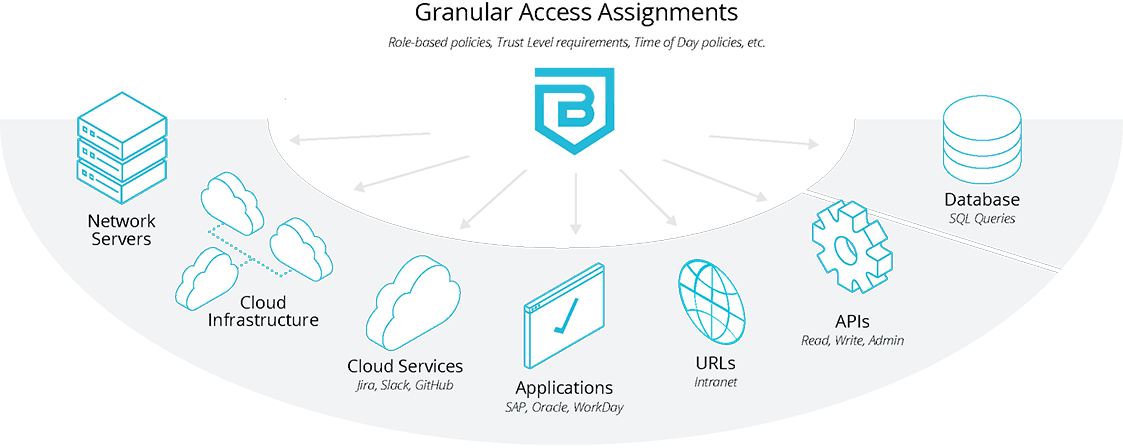
Security for All Types of Access Needs
Consistently and safely address all of the access and security needs for the growing use of third-party and outsourced personnel across your organization.
- Temporary staff, contractors, and interns
- Engineering and DevOps teams
- Project-specific partners
- Specialized consultants/auditors
Easily onboard and offboard third-parties, accommodating access without introducing complex security overhead or management. Upon contract expiration, access rights are automatically de-provisioned.
Clientless Access
With Banyan, simple, secure clientless access to websites and infrastructure is a snap – no VPNs or clunky VDI systems required. User-to-application segmentation uses least-privilege envelopes to limit exposure to specific UI and APIs. And, Banyan offers pre-built policies for common web applications like WordPress, Drupal, Jenkins, Jira, and Confluence.
Establish Conditional Trust
We believe that trust has to be based on all available information at the time access is requested. Relying on what was assumed upon initial configuration, or from the last compliance review is not enough. Banyan continuously re-authorizes access based on real-time contextual information. Access is denied when trust and security posture fails to reach the thresholds set based on your business security requirements.
Seamless User Experience and Organizational Integration
- Integrate with existing cloud, identity, and SSO tools
- End-to-end encryption, from user device to requested resource
- Users get one-click access to corporate applications, SSH, RDP, Kubernetes, and more
- Eliminate complicated virtual desktop infrastructure (VDI) environments, as the lightweight Banyan app continuously validates device security in real-time
- Easily integrate access logs into security and incident management systems with robust APIs
Getting It Just Right
Banyan’s Cloud Command Center allows quick set up and implementation. Assign least-privilege access with human readable logic statements for easy understanding and review. Define and dynamically adjust policies with changes taking effect immediately – no waiting for users to update or accept VPN configuration changes. Enable easy third-party and BYOD resource access while adhering to security and compliance requirements with the Banyan Security Platform.
Device Trust Enforcement
Designed for unmanaged devices, third-parties can download and install the lightweight Banyan app, self-register, and gain access in minutes. Built for high-security and regulated environments, Banyan can enforce specific devices be used to access resources. Device trust levels are continuously calculated and checked against policy.
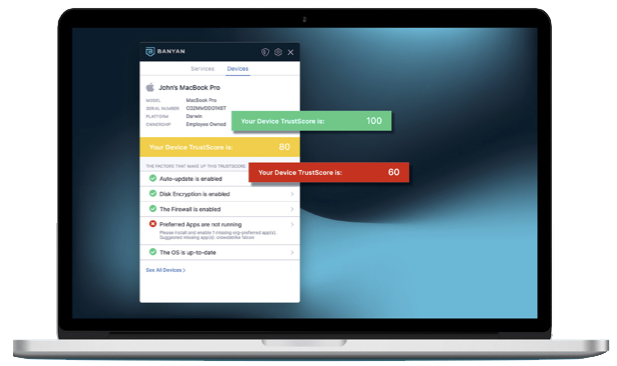
Banyan Security Zero Trust Access evaluates and provides security verification logging and alerting when access is denied due to conditional trust requirements not being met.
Download Resource