The Challenge
As organizations increasingly move their applications, resources, and data to cloud-based environments, the traditional security perimeter is becoming obsolete. The shift to remote work and the rise of distributed, cloud computing has created a new attack surface that is difficult to protect with traditional perimeter security solutions. Cloud-based environments and Software-as-a-Service (SaaS) vendors all rely on different authentication and authorization methods resulting in security and usability compromises. To address this challenge, a new approach to security and access is needed, and that approach is the modern Security Service Edge (SSE).
The Banyan Security Platform extends our industry-leading Zero Trust Network Access (ZTNA) solution providing a device centric Security Service Edge (SSE) which secures access to applications and resources from anywhere while empowering the modern workforce.
In this whitepaper, we will explore our modern approach to Security Service Edge in detail, including its architecture, benefits, and how it can help organizations improve their security posture in today’s rapidly evolving threat landscape. By the end of this whitepaper, you will have a clear understanding of how Banyan Security’s device-centric SSE helps organizations protect against modern cyber threats.
Background
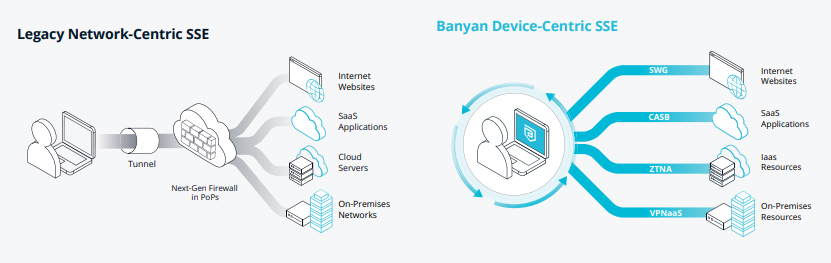
Organizations have relied on legacy approaches to securing their network perimeter. They’ve also depended on SaaS providers to provide a minimal amount of security. This has ultimately resulted in compromises to security and unsatisfactory user experiences.
While there are other vendors on the market promising to solve these problems, they usually rely on products repackaging “old school” technologies such as firewalls and edge proxies that have been virtualized, put in the cloud, and sold as a new service. Not only does this approach not
scale, but it also relies on tunnel stitching which results in poor performance and added latency. Moreover, this approach requires private corporate data to be decrypted, inspected, and then re-encrypted by the vendor before being sent to its final destination. Not only does this take
time, which again negatively impacts performance, but it has huge data privacy and sovereignty implications.
End users and the organization aren’t better off with this approach either. End users need to remember to connect using the correct agent for each resource to get basic connectivity and security. From a security perspective, this complexity often motivates end users to circumvent the supplied agent thus putting the organization at risk.
Luckily, Banyan Security is a trusted partner that understands the pains of living with legacy products, and takes pride in not having the technical shortcomings of poor approaches to SSE.
Banyan’s Approach
Banyan’s modern solution was built with ease of deployment and use in mind. It was developed from the ground up based on modern methods and technology rather than just old code, virtualized to run in the cloud. This results in exceptional performance.
Our device-centric approach is also vastly superior to competitor’s legacy models. Modern devices have the processing power to enable local functionality that improves the end user experience, minimizes the need to send traffic for inspection, and truly allows for a secure mobile workforce.

Advantages of a device-centric approach:
- Granular Control: Device-centric security provides on device granular control over the security settings and policies for each individual user, device, and resource ensuring that they are protected against potential threats.
- Enhanced Visibility: The device, being the source of traffic and resource interactions, is the ideal place to learn about where they are going, and what they are doing once they access the resources.
- Improved Compliance: Device-centric security helps organizations meet regulatory and compliance requirements by ensuring that devices are configured to meet industry standards and best practices while also enforcing acceptable use policies (AUPs).
- Protection against Advanced Threats: Device-centric security helps protect against advanced threats, such as zero-day attacks and advanced persistent threats, by providing enhanced security features and continuous monitoring, and blocking outbound traffic attempts even when users click on links they shouldn’t.
- Improved User Experience: Device-centric approaches improve the user experience by providing secure access to corporate resources from any device, anywhere, with minimal client or agent interaction. Convenient access and always-on security are provided even when a user is not logged in to the agent.
- Cost-Effective: Device-centric security is more cost effective than traditional network-centric security approaches, as it reduces the need for costly security appliances, lowers cloud service provider (CSP) traffic charges, and improves overall security posture.
Banyan’s approach, which does not require traffic to be routed to our cloud for inspection results in more uptime and stability. Many customers have come to us after putting up with unplanned outages resulting in lost revenue, increased helpdesk calls, and unhappy executives and employees.
Banyan Security Platform
The Banyan Security Platform securely connects users to applications, resources, and infrastructure while protecting them from internet threats. Risk and security are continuously evaluated and enforced in real-time across hybrid, multi-cloud, and SaaS environments.
The Banyan solution provides the following capabilities:
- Zero Trust Network Access (ZTNA) – application and infrastructure access – simple, least privilege access to applications and services across hybrid- and multi-cloud infrastructure, leveraging your existing enterprise identity and security tool investments.
- Virtual Private Network as a Service (VPNaaS) – network access – modern, high-performance, tunnel based access to networks, incorporating zero trust enhancements like continuous authorization and device trust.
- Cloud Access Security Broker (CASB) – SaaS application access security – layered security that provides easily managed controls for who, using what specific devices, can access your SaaS applications.
- Secure Web Gateway (SWG) – internet threat protection – protects users from being phished, straying onto malicious web sites, and ransomware exposure. Organizations can also block specific categories of web sites, like gambling and pornography.
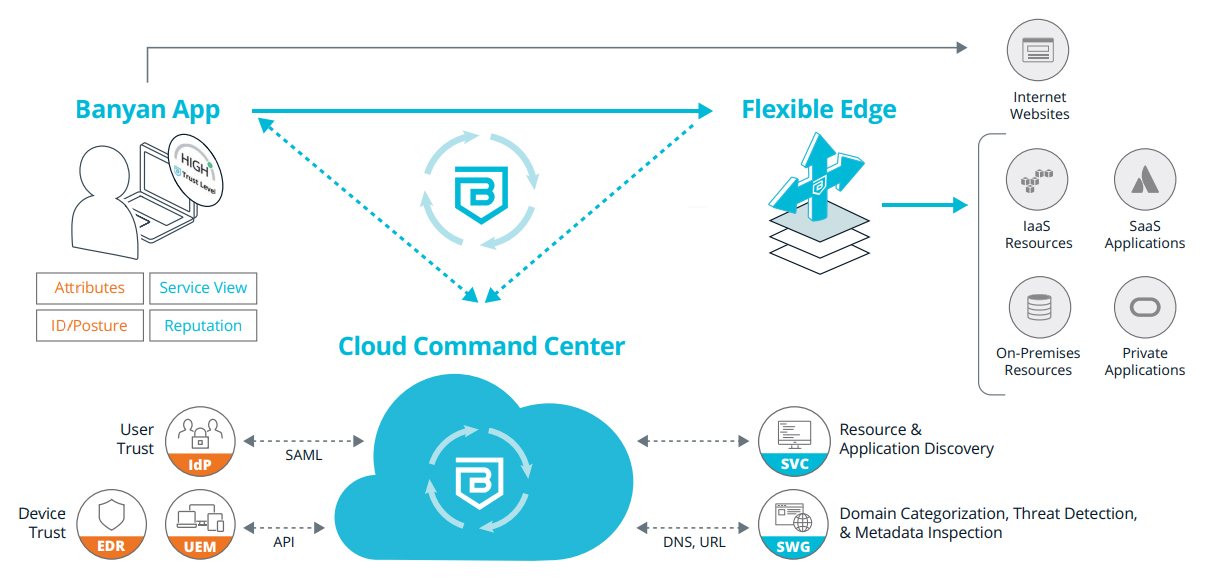
The Banyan solution provides the following capabilities:
- Cloud Command Center – Centralized dashboard and policy engine provides least-privileged access to sensitive corporate applications and resources.
- Banyan app – Real-time risk metric computation algorithms, continuously updated to quantify and score user/device context and behavior.
- Flexible Edge – A multi-cloud identity-aware access proxy that securely cloaks cloud applications and servers from malicious attacks or inadvertent exposure and also provides real-time enforcement of accessibility due to policy infractions.
- Threat feeds – A collection of direct and third-party information used to learn about existing traffic flows and websites and make real-time threat and risk decisions.
- Integrations – Industry standard methods such as APIs, SAML, and OIDC are used to help deploy, manage, and secure our solution end-to-end. These integrations also share intelligence, taking advantage of existing network and security investments.
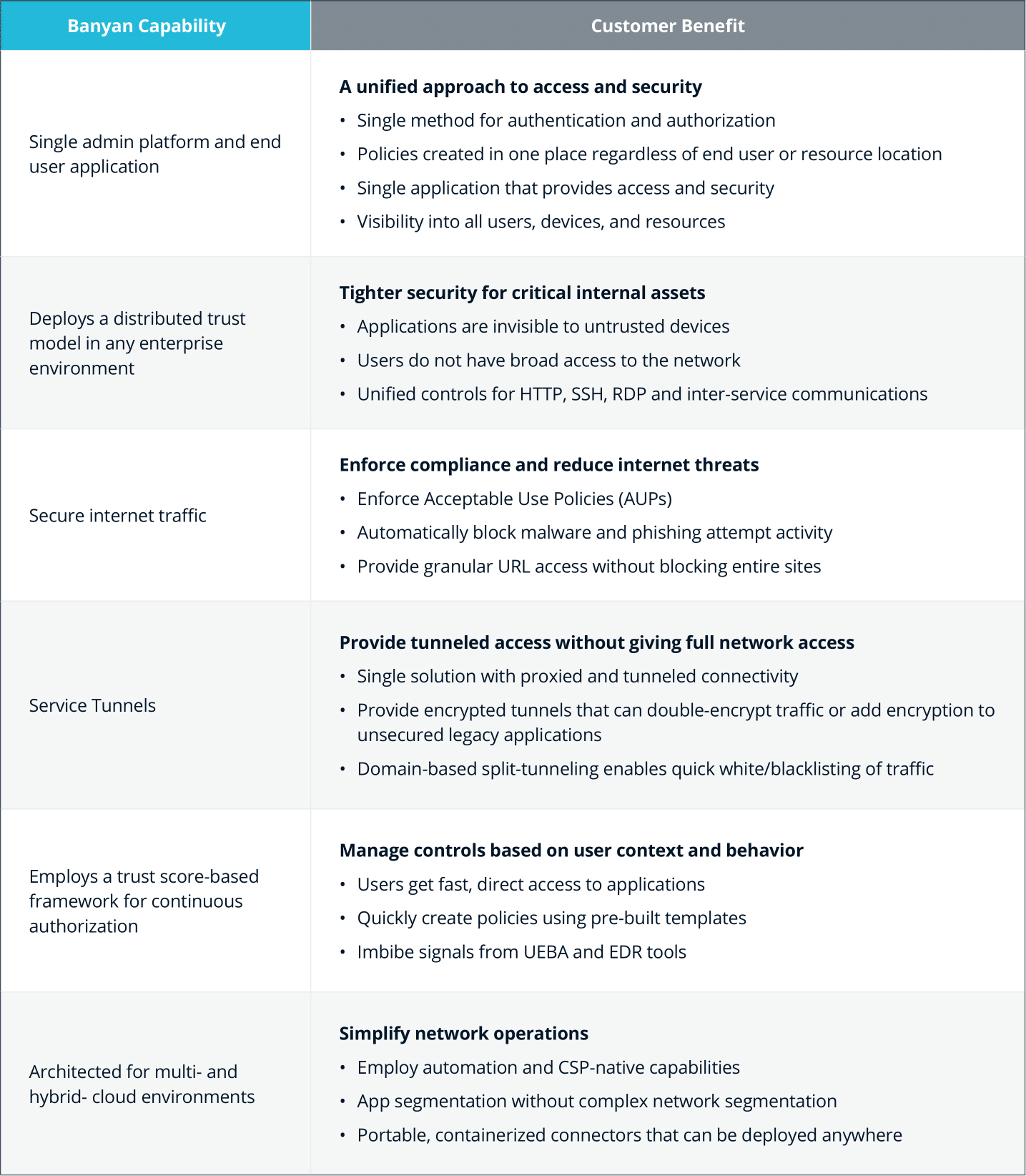
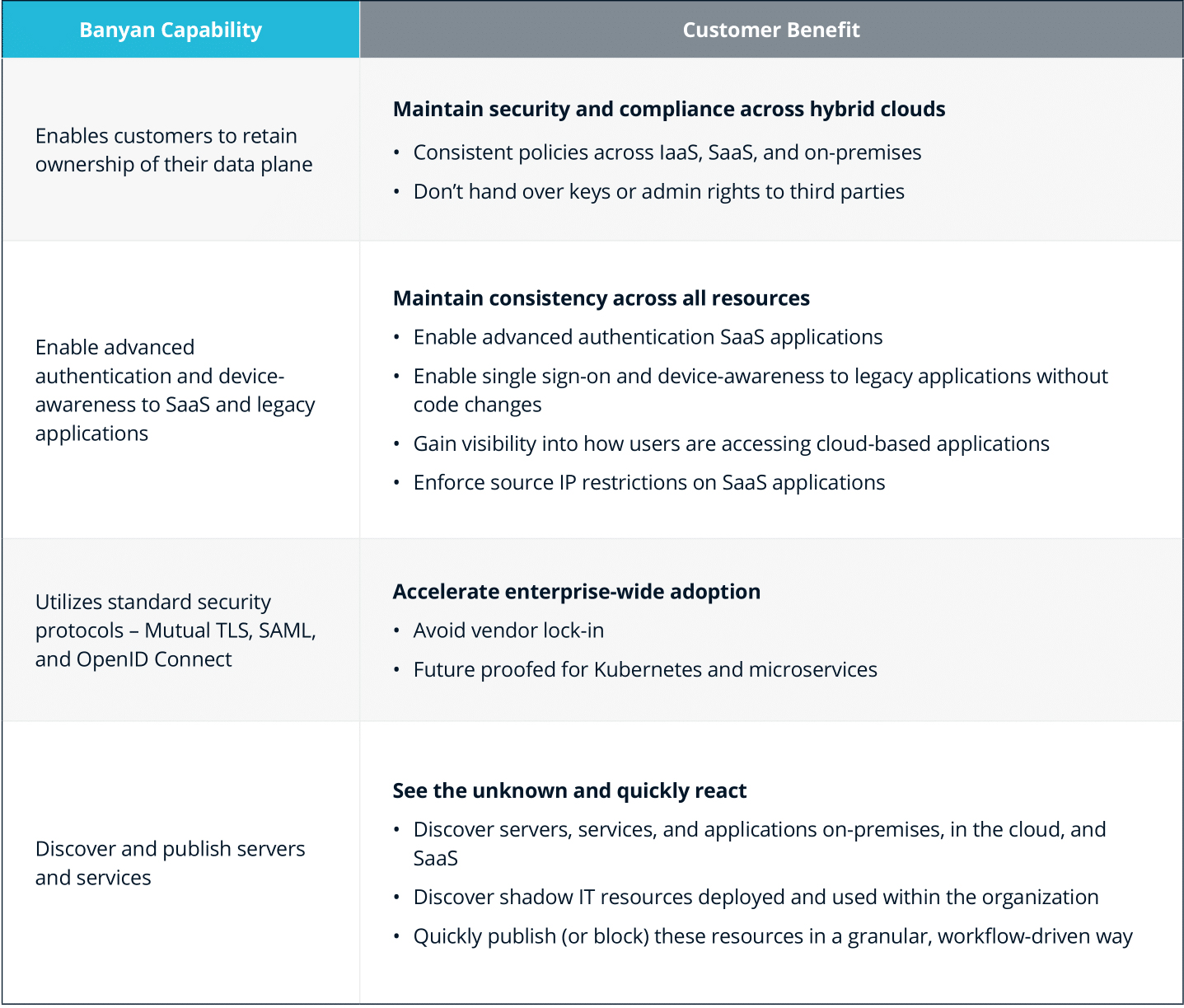
Key Benefits
The Banyan Security Platform provides impactful benefits to both organizational security and user experience.
The Banyan Difference
The Banyan Security Platform is trusted by organizations of all sizes and in all verticals, around the world because of these uniquely valuable differences:
Device-Centric Approach
- Network simplicity and superior performance is achieved by limiting traditional network bottlenecks, eliminating unnecessary hops, and avoiding concentrators
- The compute power of modern devices is leveraged to enable risk-based routing. Making decisions at the traffic source lowers bandwidth consumption, sending traffic direct to destination. No need to send everything to a third-party cloud first of devices
- Privacy is safeguarded by building intelligence into the on-device app, rather than the cloud. Full-stack platform portability also means full data sovereignty.
Advanced Security
- Device trust is enforced in real-time using continuous authorization against granular Trust-Based Access Control (TBAC) policies.
- Only Banyan Security offers zero trust access that spans hybrid, multi-cloud, and SaaS-based environments.
- Always-on threat and malware security that doesn’t require logging in to an agent.
- Double encryption of secure transport protocols such as HTTPS and SSL.
- Multi-factor authentication based on user and device factors.
- Harden edge connectors that only allow outbound session initiation.
- Sessions based on short-lived X.509 client certificate in the TLS handshake.
- Real-time domain categorization for DNS and content filtering.
- Source IP validation for SaaS application access.
Flexible Architecture
- The Flexible Edge – Banyan’s mesh architecture extends security controls to distributed assets, spanning all environments and protocols. The cloud-native approach leverages the public internet without requiring network tunnels or MitM clouds resulting in a highly performant,
yet scalable solution that doesn’t risk privacy or data sovereignty. Only Banyan flexibly supports cloud IaaS (Global Edge) while also offering the option for enterprises to self-host their edge (Private Edge).
“The increased security we get with Banyan is tremendous. Compared to our VPN it’s night and day.”
Easy to Deploy and Use
- Get deployed in 15 minutes or less.
- One-click access to infrastructure and applications – Banyan integrates with customer IaaS and PaaS environments providing one-click access to applications and resources including SSH/RDP servers, VNC, Kubernetes, and databases – even SaaS applications are protected. Least privilege access allows differentiated access for FTEs and third parties alike that is a snap to deploy, administer, and audit.
- Service Tunnel offers a super-easy transition from legacy VPNs toward zero trust. It delivers high-performance, tunnel-based access to networks, and is built on a modern WireGuard foundation with continuous authorization and device trust enhancements.
- Fast, easy, and secure one-click passwordless access to hosted websites, IaaS infrastructure, and SaaS applications. Even complex datacenter and IaaS environments are a snap.
- Service Catalog simplifies access to Windows, Linux, and Kubernetes environments, including developer tools like GitLab, Jira, and Jupyter.
- Automated discover and publish capabilities enable administrators to inventory and rapidly make ephemeral applications and IaaS resources available to users.
- User-visible trust level enables self-remediation of device posture issues.
- Support for clientless deployment.
- Terraform support for automated deployment of zero trust security policies. Think of this as “zero trust as code”.
Conclusion
Banyan Security has created a platform providing modern Security Service Edge (SSE) functionality, built for the cloud from the ground up. Our platform offers industry-leading VPNaaS, ZTNA, CASB, and SWG without sacrificing user and administrator satisfaction or compromising security.
Our device-centric approach is praised by customers for its simplicity and superior performance.
The modern Banyan Security Platform uniquely provides teams all the tools needed to secure access to applications and resources from anywhere while empowering your modern workforce of today and tomorrow.
Quickly provide your workforce secure access to corporate resources and infrastructure.
