What is CASB?
A Guide to Cloud Access Security Brokers (CASB)

What is a Cloud Access Security Broker?
A CASB (Cloud Access Security Broker) is a solution for controlling the access and overlaying security to a SaaS (Software-as-a-Service) application or resource. The CASB provides visibility to not only what SaaS applications corporate users are accessing but can also provide visibility into what users are doing when on the SaaS application. CASB allows the organization to create policies that ensure the correct users are accessing authorized resources and data in SaaS applications.
Ideally, access and security policies for on-premises and SaaS applications and resources are aligned.
What challenges does CASB help solve?

Visibility – Remote work and BYOD are creating a greater need for organizations to know what’s happening in their cloud environments. Unmanaged devices abound, and without proper visibility into your deployments, you run the risk of allowing unwanted access. A CASB discovers your organization’s cloud app usage, creates reports on cloud spend, and performs risk assessments to let you decide whether an app should be blocked.

Compliance – Cloud computing services require a large and growing number of compliance and regulatory conditions be met in order to operate at an organizational level. This is particularly true in the public sector as well as the financial services and healthcare industries. A CASB can identify the greatest risk factors in your industry and set stringent data protection policies to achieve and maintain compliance across your organization.

Data Security – Every two years, the volume of the world’s data doubles in size. This exponential increase in data has seen bad actors become craftier than ever before. Combining a CASB with cloud Data Loss Prevention (DLP) lets you not only see potential data risks but stop them, too. What’s more, you have visibility into sensitive content traveling to or from the cloud or between clouds, giving you the best chance to identify incidents, apply appropriate policy, and, above all, keep data secure.

Threat Protection – Cloud threats and malware are rampant in today’s IT ecosystem, and in most cases, cloud resources are the most vulnerable. A CASB gives you the power of behavior analytics and threat intelligence to turbocharge your cloud security. With these advanced capabilities, you can quickly identify and remediate suspicious activity, keep cloud applications and data secure, and bolster your organization’s overall cloud security posture.
Other vendors may frame the above as Identity, Visibility, Data Protection and Threat Protection depending on their offering and capabilities.
How do CASBs differ from traditional network security perimeters?
A traditional network security perimeter is used to protect network infrastructure, servers, and applications that are managed and hosted by an organization, either in a company-owned lab, third-party co-location lab, and even Infrastructure-as-a-Service (IaaS) deployments managed by the organization. While IaaS uses a “shared responsibility” model for protection resources and services, the organization is still responsible for making sure that the appropriate security models are protecting applications built on the IaaS.
CASB can be thought of as protecting everything that is outside of the above mentioned managed and hosted services. CASB will be protecting SaaS applications where an organization pays a company for the right to use its cloud-based software. Examples of these are Office365, Google Workspace (formerly G-Suite), Salesforce, and Box. An organization cannot directly control what the SaaS vendor does to protect its infrastructure, so a CASB can be used in the various ways mentioned above.
How does a Cloud Access Security Broker work?
A CASB can be implemented via APIs and forward and/or reverse proxies.
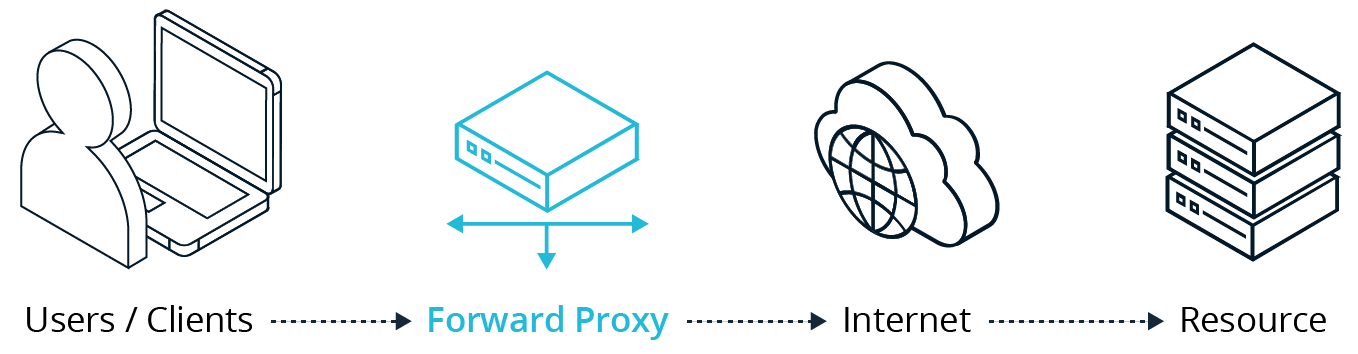
Forward proxy – A forward proxy offers DLP in real time for both sanctioned and unsanctioned applications, but only applies to managed devices, and cannot scan data at rest. Forward proxy deployment can be done using PAC files, DNS URL redirect, or agents.
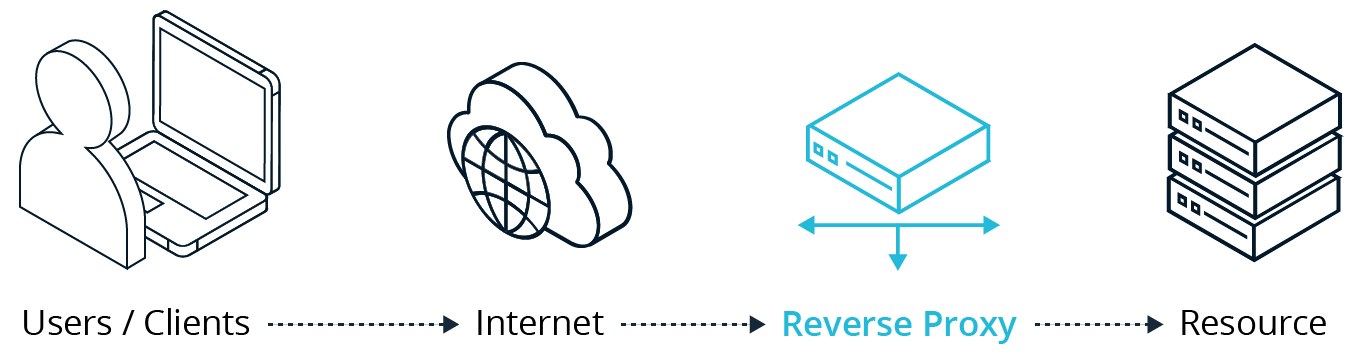
Reverse proxy – A reverse proxy redirects all user traffic, and therefore works for both managed and unmanaged devices. It offers DLP in real time, but only on sanctioned applications.
Additionally, one can use proxy-based CASBs to make changes to the application data stream to add additional controls, such as encryption, as well as record and monitor events that happen within the application, such as access attempts, logins, or use of functionality
What challenges may limit deploying a CASB?
All technologies come with challenges and in the case of CASB, the challenges are with implementation and functionality support.
Some SaaS providers, such as Microsoft for 0365 and Google Workspace (formerly G-suite), have made it a challenge to use CASB proxies by their use of certificate pinning. Certificate pinning is a technique that reduces the risk of a man-in-the-middle attack, compromise of certificate authorities, and mis-issuance of a certificate that accepts only authorized certificates for the client and browser connections. These vendors are providing some lightweight controls similar to CASB in higher tiers of their product offerings.
With CASB proxies being limited, this leaves APIs. CASB APIs rely heavily on what the SaaS applications support. For example, a corporate policy could state that a SaaS application must ensure safe collaboration and data sharing practices in the cloud when the user is a contractor. This could mean that if the SaaS application has “share” functionality, we would like this to be limited to emails in our organization only. This would be done use a CASB API call to tell the SaaS application to enforce this for the specific contractor. The CASB may have a way to configure this policy but a particular SaaS application may not support this so there will be some compromises on corporate policy.
How is a CASB different from a Secure Web Gateway (SWG)?
SWG (Secure Web Gateway) and CASB (Cloud Access Security Broker) are two different types of security solutions that serve different purposes, although there is some overlap between their features. Here’s a comparison of the two:
- Focus: SWG is primarily designed to secure web traffic by filtering and monitoring web traffic, while CASB is focused on securing cloud-based applications and services.
- Deployment: SWG solutions are typically deployed on-premises or in the cloud, while CASB solutions are usually cloud-based and sit between users and cloud-based applications and services.
- Features: SWG solutions typically include features such as URL filtering, content filtering, SSL/TLS inspection, and advanced threat detection. CASB solutions, on the other hand, offer features such as cloud application visibility and control, data loss prevention (DLP), user behavior analytics (UBA), and identity and access management (IAM).
- Use cases: SWG solutions are commonly used by enterprises and other organizations to provide secure internet access to their employees, partners, and customers. CASB solutions are typically used to secure access to cloud-based applications and services, especially in scenarios where sensitive data is stored or accessed through these services.
In summary, SWG and CASB solutions serve different purposes, but can complement each other in some scenarios. For example, a company that uses cloud-based applications may use both SWG and CASB solutions to secure its web traffic and cloud-based applications respectively.
