FAQ
Frequently asked questions about all things zero trust and security service edge (SSE)What is Zero Trust?
TL;DR: Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, validated, and continuously authorized leveraging user and device trust along with device security posture against a backdrop of resource sensitivity before being granted or keeping access to applications and data.
More detail: broadly speaking, the theme of Zero Trust is the reduction of implicit trust. It is an information security model that denies access to applications and data by default. Threat prevention is achieved by only granting access to networks and workloads using policy informed by continuous, contextual, risk-based verification across users and their associated devices. Zero Trust advocates these three core principles: All entities are untrusted by default; least privilege access is enforced; and comprehensive and continuous security monitoring is implemented.
A Zero Trust framework moves away from one-time security gating decisions toward continuous assessment of the risk level of the user and device, dynamically adapting access privileges based on changes in the risk level.
What is the goal of Zero Trust?
The fundamental purpose of Zero Trust is to understand and control how users, processes and devices engage with data, thereby proactively reducing the risk of a data breach and its spread. Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, validated, and continuously authorized leveraging user and device trust along with device security posture against a backdrop of resource sensitivity before being granted or keeping access to applications and data.
Adopting Zero Trust enables organizations increase their level of continuous authorization, enabling them to respond to intrusions and exploits quickly in order to help stop attacks before they can succeed:
- Phishing emails targeting employees
- Lateral movement through corporate network
- Redirecting a shell to a service to compromise a corporate machine
- Lost or stolen application, database service credentials
- Exfiltration of database via compromised application host
- Compromising application host via privileged workstation
- Using developer password to elevate application host privileges
- Installing keylogger via local privilege escalation on workstation
What is the history of Zero Trust?
The concept of “Zero Trust” was popularized by an analyst at Forrester Research Inc, in 2010 Google was one of the first companies to take notice of the potentialities of the Zero Trust architecture. They started an initiative called BeyondCorp, and in 2014, Google implemented a de-perimeterized framework based on the Zero Trust Architecture. BeyondCorp by Google, is an implementation of zero-trust security concepts creating a Zero Trust network.
As part of the evolution of Zero Trust security, the work of National Counterintelligence and Security Center (NCSC) and National Institute of Standards and Technology (NIST) on the Zero Trust Model led to the creation of a publication titled – Zero Trust Architecture. In this publication, Zero Trust is defined as a collection of principles that can be applied to network security. The six key tenets include:
- Defining Devices. For Zero Trust to be implemented fully, the enterprise needs to consider all data sources and computing services as resources. These may include devices that share data with aggregators, software as a service (SaaS), and different types of endpoints that connect and communicate with the network.
- Securing Communications. All access requests from assets must meet preset security requirements. The assets may be located on enterprise-owned network infrastructure or any external network – the same security verifications must be applicable to all. Trust can never be implicit.
- Session-Based Resource Access. Trust has to be established before authorizing access to any enterprise resource, and the trust must be applicable only for the duration of the transaction. Authorization of access to a specific resource cannot be extended to access a different resource.
- Attribute-Based Policy Enforcement. Policy is the set of access rules based on attributes that an organization assigns to a user, data asset, or application. These attributes could be device characteristics like software version, location, time of request, etc. Behavioral attributes defined by user and device analytics may also be considered based on sensitivity of the resource.
- Dynamic Authentication and Authorization. Granting access, scanning and assessing threats, and continually reevaluating trust must be an ongoing process. Asset management systems and multi factor authentication (MFA) need to be in place along with continuous monitoring to ensure that re-authentication and reauthorization are based on defined policies.
- Policy Fine-Tuning. Enterprises must collect as much information as possible about the current state of the network and communications, using this data to continually improve their security posture. Insights provided by this data help to create new policies where needed and fine-tune existing security policies to enforce proactive protection.
The pandemic has accelerated digital transformation and telework on a scale never seen before. Employees are working from anywhere and collaboration in the cloud has skyrocketed. This new environment has expanded the cyber attack surface, compromising critical United States (U.S.) infrastructure and the lives of our citizens. The recent slew of major 2021 cyberattacks including those of SolarWinds, Microsoft Exchange and Colonial Pipeline, has moved cybersecurity improvements on the top of the agenda for the U.S. federal government.
One of the most influential catalysts for Zero Trust is the recent executive order by the U.S. government. In May 2021, President Joe Biden signed an Executive Order to strengthen U.S. cybersecurity defenses. This order requires agencies to have a plan to adopt a Zero Trust framework within 90 days. It also provides clear recommendations and timeframes for public and private organizations to implement key technology and process improvements.
As a result, a growing number of enterprises are considering adopting a Zero Trust network architecture as a key component of their enterprise security strategy.
Why do enterprises need to adopt a Zero Trust approach?
Enterprise network complexity has outstripped legacy methods of cybersecurity as there is no single, easily identified perimeter for enterprises. As a result, security teams are shifting network defenses toward a more comprehensive IT security model to secure their data and systems, which means building a dynamic, modern security architecture that builds trust on a much broader and deeper basis than traditional security measures.
The Zero Trust approach enables organizations to restrict access controls to corporate resources including applications and environments without sacrificing performance and user experience. Simply stated, it’s an approach that trusts no one.
As more and more organizations leverage cloud computing, the traditional network security perimeter has all but vanished, and security teams are finding it difficult to identify who and what should be trusted with access to their networks. As a result, a growing number of organizations are adopting a Zero Trust network architecture as a key component of their enterprise security strategy.
Why is Zero Trust a model for more effective security?
A Zero Trust approach implicitly trusts no one. As more organizations do more computing outside traditional perimeters and in the cloud, security teams find it increasingly difficult to trust or identify who and what should be allowed or trusted with access to their networks.
Without Zero Trust, users are granted privileges to infrastructure and data just once and security teams have limited visibility into what the user or device is doing. Without reverifying the risk level, the user is free to access any resources, regardless of any change in user or device trust. If a cyberattacker subverts the device or user account, then the attacker can easily move laterally and likely to go undetected, resulting in a breach.
What are the common security principles of a Zero Trust environment?
- Least Privilege Access – any user, program, or process should have only the bare minimum privileges necessary to perform its function or task.
- User Trust – User authentication is dynamic and strictly enforced before access is allowed; further access authorization is continuously re-evaluated – a constant cycle of access, scanning and assessing threats, adapting, and if necessary, revoking access in real-time.
- Device Trust – Device trust complements user trust by uniquely identifying each device and quantifying its security posture. Doing so allows specification of minimum security posture levels via granular Trust-Based Access Control policies.
- Continuous Authorization – rather than being a single event during access requests, continuous authorization changes this perspective to an on-going, real-time process where the user, device, and resource contexts are constantly being re-evaluated and access terminated if any relevant contextual factor falls below policy thresholds.
Why is Zero Trust a model for more effective security?
A Zero Trust approach implicitly trusts no one. As more organizations do more computing outside traditional perimeters and in the cloud, security teams find it increasingly difficult to trust or identify who and what should be allowed or trusted with access to their networks.
Without Zero Trust, users are granted privileges to infrastructure and data just once and security teams have limited visibility into what the user or device is doing. Without reverifying the risk level, the user is free to access any resources, regardless of any change in user or device trust. If a cyberattacker subverts the device or user account, then the attacker can easily move laterally and likely to go undetected, resulting in a breach.
What is the difference between traditional VPN products and modern ZTNA solutions?
VPNs are the traditional choice for remote access because they work well with legacy perimeter-based security models. However, they have numerous limitations that make them ill-suited to the security and remote access needs of the modern enterprise, including:
- Perimeter-focused security: VPNs help reinforce the traditional perimeter-based security model because an authenticated user is granted full access to the corporate network. This allows an attacker to move laterally through the corporate network after gaining access via compromised VPN credentials or exploitation of a VPN vulnerability.
- Network-level access controls: VPNs implement access controls at the network level without visibility into or control over the application layer. This provides overly-permissive access to users, granting read, write, and execute access to resources within different applications.
- No cloud support: VPNs are typically designed to provide secure remote access to the corporate network. Often, they have limited support for cloud-based resources located outside of the traditional perimeter.
- Poor BYOD support: Allowing BYOD devices to access the corporate VPN provides access to corporate resources from unmanaged, non-corporate endpoints. This may allow malware or other cyber threats direct access to the corporate network.
- VPNs are complex and costly to manage and scale: legacy VPNs require an investment in equipment, complex network security policies, along with an agent for every endpoint, which create an administrative IT support burden with the expansion of the remote workforce.
Modern remote access solutions ensure simple, scalable, context-aware and data-centric application access, directly engaging the principle of least privilege and optimizing security controls. They also address today’s complex, hybrid work environments to facilitate an adaptive, secure and flexible Zero Trust strategy. Benefits over VPN include:
- Simple to deploy and configure
- Easy to manage and maintain
- Protects underlying network
- Rapid scalability and provisioning
- High performance for both on-premises and remote workers
What is Zero Trust Network Access?
Zero Trust Network Access (ZTNA) is a category of technologies that provides secure access to applications and services. ZTNA allows “least privilege” access to specific applications and resources, and not the entire underlying network to any user with valid login keys, thus reducing the attack surface and preventing lateral movement of attacks from compromised accounts or devices. ZTNA builds upon the concept of “Zero Trust,” that asserts that organizations shouldn’t trust any entity, whether inside or outside the security perimeters, and instead must verify every user or device before granting them access to sensitive resources, ensuring data safety and integrity.
Unlike VPNs which grant complete access to a LAN, ZTNA solutions only permit access to those specific services that the user has been granted access to. In a ZTNA system, access depends on user and device identity, device security posture, factoring in application sensitivity, regardless of network location or application hosting model. ZTNA shifts the focus to accessing specific applications rather than creating a tunnel into your network. Security features like least privilege access (LPA), continuous authorization, device trust, granular enforcement, and dynamic trust scoring are all part of a robust ZTNA solution.

Why is continuous authorization with device trust important?
Relying solely on user credentials means that anyone, legitimate or not, in possession of them has unfettered access to enterprise infrastructure. Continuously re-verifying credentials, and incorporating the risk level of the user’s device provides security teams much-needed visibility into what the user and device are doing. In this model, Zero Trust employs the principle of least privilege, only giving each user access to what they need to do their job. In contrast, with a legacy VPN in place, when a cyberattacker subverts a user account or device, the attacker can easily move laterally and likely venture undetected, resulting in a breach. One example of this is the Colonial Pipeline ransomware attack in June 2021, where all it took was an inactive employee’s stolen login credentials to halt their operations, which provides 50% of the gas, jet fuel, diesel and heating oil for the Eastern United States – it remains the largest compromise of U.S. critical infrastructure to date.
What is the difference between authentication and authorization?
Authentication and authorization are two related but distinct concepts in computer security that are often used together to control access to resources.
Authentication refers to the process of verifying the identity of a user or device. This involves presenting credentials, such as a username and password, a digital certificate, or a biometric identifier, to a system. The system then compares the credentials to a stored record or a trusted identity provider to determine if the user is who they claim to be. If the credentials are valid, the user is granted access to the system.
Authorization, on the other hand, refers to the process of determining what an end user or device is allowed to do on a system. This involves defining rules or policies that specify what resources the user is allowed to access and what actions they are allowed to perform on those resources. Authorization is typically based on the user’s role, group membership, or other attributes that define their level of access.
First we authenticate, then we authorize.
How can Banyan Security help enterprises adopt a Zero Trust architecture?
Banyan Security is on a mission to enable the modern workforce to securely and easily access the applications and services they need while working from wherever they are. The Banyan Security Platform provides fast, easy provisioning of user-to-application segmentation, giving users and their devices secure, one-click access to enterprise applications resources and infrastructure from anywhere – without requiring network-centric technology such as Virtual Private Networks (VPNs). Risk and security are continuously evaluated and enforced in real-time across hybrid, multi-cloud and Security-as-a-Service (SaaS) environments.
What is Least Privilege Access?
A core principle of zero trust, which refers to the concept and practice of restricting access rights for users, accounts, and computing processes to only those resources absolutely required to perform routine, authorized activities.
What is Cloud VPN?
Also called a cloud-based VPN or VPNaaS, it is a newer type of VPN technology that securely connects a remote workforce to an organization’s networks, applications, and the internet through a cloud-hosted VPN.
What is Remote Access?
Remote access is the ability to access a computer or device from another device, at any time, and from anywhere. With remote access software installed on your computer, you have the freedom to access that computer, and all its files and applications, from another device and control it as if you were sitting in front of it.
What is BeyondCorp?
BeyondCorp® is a cybersecurity architecture developed at Google that shifts access control from the traditional network perimeter to individual devices and users. The goal is to enable users to securely work anytime, anywhere and on any device without having to use a virtual private network, or VPN, to access an organization’s resources.
What is VPN as a service (VPNaaS)?
Also known as Cloud VPN or hosted VPN – is a new type of VPN technology specifically designed for the cloud. A cloud VPN enables users to securely access a company’s applications, data and files in the cloud through a website or via a desktop or mobile application.
What does Banyan Security do?
Today’s computing world has become truly perimeter-free. Remote employees and contractors in coffee shops, airports, and homes access internal applications running in multiple public clouds, connecting to other cloud applications and enterprise data centers. Mobility, containers, and public and private clouds have unleashed innovation like never before.
Yet this creates tremendous challenges for securing this ever-growing and interconnected access surface to protect information, ensure compliance, catalyze innovation, and deliver an outstanding user experience.
At Banyan Security, we help IT and Security teams successfully deliver modern secure remote access to both today and the next generation of users and applications.
Our Security Service Edge (SSE) solution – the Banyan Security Platform – provides secure, zero trust “work from anywhere” access to applications and resources for employees and third parties while protecting them from being phished, straying onto malicious web sites, or being exposed to ransomware. A Flexible Edge architecture enables rapid, incremental deployment on-premises or in the cloud without compromising privacy or data sovereignty. A unique device-centric approach intelligently routes traffic for optimal performance and security delivering a great end user experience. Built on a patented Zero Trust architecture, the Banyan solution transparently deploys in hybrid and multi-cloud environments, continuously enforcing trust-based access policies based on any combination of user, device, and application contexts.
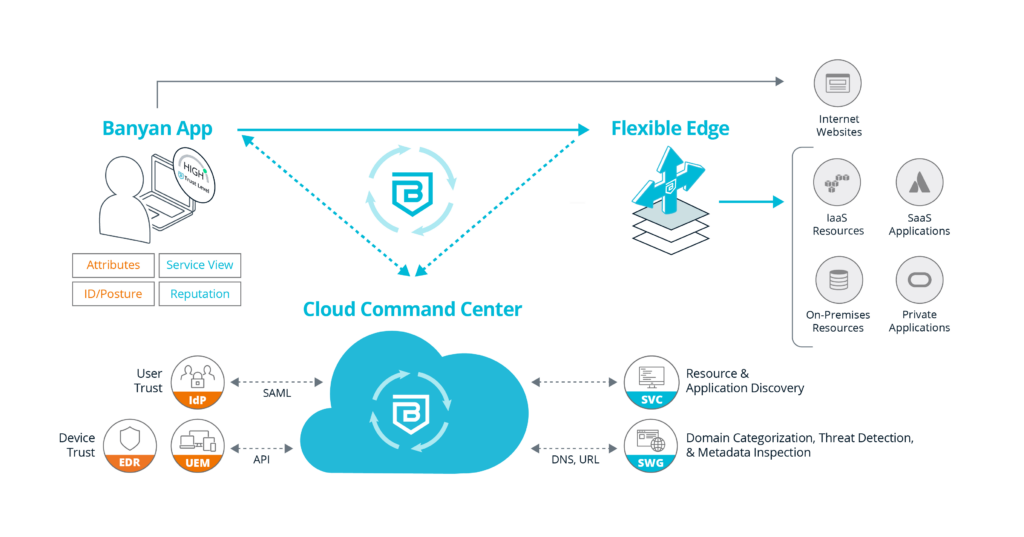
How does the Banyan Security Platform work?
- The Cloud Command Center is our cloud-based management and visibility platform which integrates with various services, such as IdP, EDR, and UEM to learn about the user and devices. It also integrates with threat feeds to provide enforcement policies on outbound traffic. The Cloud Command Center also provides discover and publish functionality, allowing enterprises to quickly locate resources and create least privilege access to them, whether they are on-premises, in SaaS, or IaaS.
- Flexible Edge enables easy deployment anywhere your resources live. The Flexible Edge provides a multi-cloud identity-aware access proxy that securely cloaks cloud applications and servers from malicious attacks or inadvertent exposure and also provides real-time enforcement of accessibility due to policy infractions. Flexible Edge can be easily deployed using tarball, Docker, and Terraform.
- The Banyan app, available on desktop and mobile, is recommended but not required. The Banyan app provides VPNaaS and ZTNA connectivity, along with making SWG and CASB decisions. The Banyan app is also used to gain visibility into the device for real-time Device Trust insights. The Banyan app communicates with the Cloud Command Center for authentication and authorization decisions, aka control plane communication. It also communicates directly with the Flexible Edge for all data plane related activities.
#image_title
Can I replace my legacy VPN with the Banyan Security Platform?
The Banyan Security Platform enforces least-privileged access to applications and services in real-time, leveraging your existing enterprise identity and security tool investments. Built on a patented zero trust architecture, the Banyan solution transparently deploys in hybrid and multi-cloud environments, continuously enforcing trust-based access policies based on any combination of user, device, and application contexts.
Can I deploy ZTNA and keep my existing VPN?
No problem! The Banyan Security Platform’s Zero Trust Network Access (ZTNA) capabilities can be deployed alongside existing infrastructure – no need to rip and replace. Banyan offers an incremental “deploy-as-you-go” model for admins and users that includes co-existence with VPNs, one app or service at a time, permissive mode (learning) vs. enforcing, and more.
Is an endpoint client required for the Banyan Security Platform?
Banyan’s Security Service Edge (SSE) solution can be deployed without an endpoint client; however, you get some important benefits by using the lightweight Banyan app. Banyan delivers a robust Device Trust solution featuring passwordless access that takes advantage of a lightweight app that can be easily installed by the end user or silently deployed by the administrators. Unlike MDM and UEM products, the Banyan app does not provide any administrative control over the end user’s personal device, making it attractive for employer-owned and BYOD (employees, contractors, etc.) devices alike.
What is the Banyan app? Is it required?
The Banyan app is a cross-platform endpoint client, installed on end user desktop and mobile devices. The app is used to register and authenticate end user devices with the Banyan Cloud Command Center. Note that the Banyan app is optional on MDM-managed devices on which you can install a Device Certificate via your device manager.
The Banyan app allows users to self-register devices and enjoy one-click access to a personalized catalog of corporate resources (websites, applications, services, infrastructure, etc.)
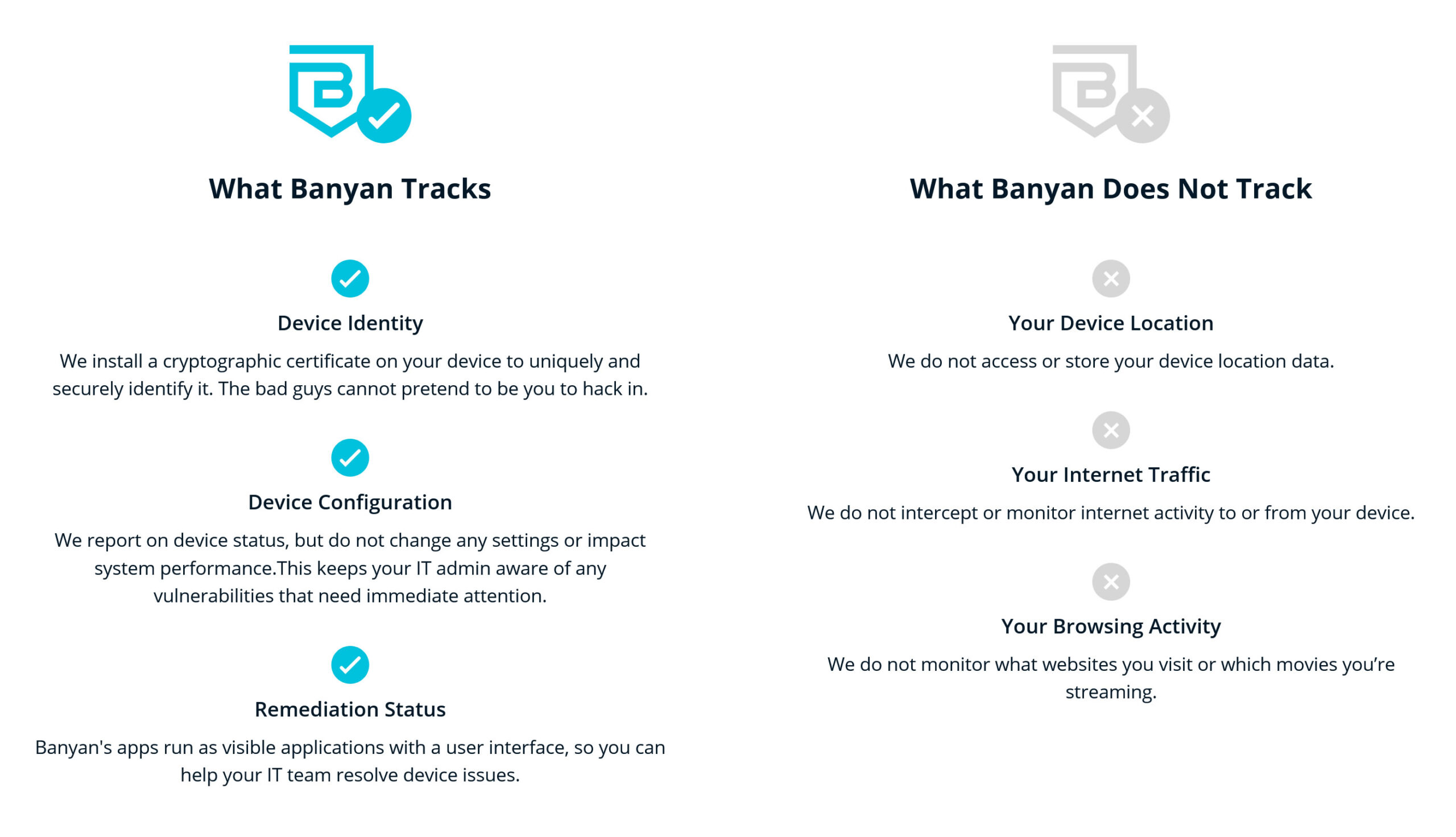
Should users be concerned about privacy with the Banyan app?
The Banyan app was developed with privacy in mind.
How do I manage the Banyan Security Platform?
The Banyan Cloud Command Center is the central management console for IT Administrators and Security teams. You can interact with the Command Center via the web portal or the RESTful API, to develop and enforce policies, configure alerts for security events and visualize real-time connectivity.
The Cloud Command Center is a SaaS platform, connected with your enterprise identity provider, that lets users write granular policies based on user and device entitlements. The Command Center issues short-lived tokens and certificates, offering one-click access to applications and resources, while also ensuring every access granted is continuously authenticated and authorized.
What kind of automation capabilities are available in the Banyan Security Platform?
- Discover and Publish provides a streamlined way to secure access to hybrid and multi-cloud infrastructure. Banyan Security is providing customers with the following benefits:
-
- Improved time to value – Banyan Security provides a quick and effective way to create least-privileged access to your infrastructure and services.
- Scalable IaaS access management – Banyan Security provides a modern, consistent way to manage access to IaaS workloads across any cloud.
- RESTful APIs from Banyan automate security policies
- Terraform Support – Terraform is an “infrastructure as code” tool that lets admins define corporate resources in human-readable configuration files. A Terraform Provider is a plugin that lets users manage external APIs, facilitating Terraform’s communications with various cloud providers, databases, and services. Learn more here.
How do I get started?
Banyan can help you identify a meaningful remote access project and configure your environment for a zero trust security posture. And best of all, it is designed for an incremental rollout in any environment, integrating with existing EDR, MDM/UEM, and SIEM solutions. You can even deploy it alongside your existing VPN as you evolve your network infrastructure.
Speak with our Zero Trust experts about your security initiatives.
Get Started now with a free trial of the Banyan Security Platform Team Edition.
Can I really deploy Banyan Security’s solution in less than 15 minutes?
Yes! You can get the Banyan Security Platform Team Edition installed, deployed and adding value in less than 15 minutes. Here’s a video showing Dr. Chase Cunningham deploying the Banyan solution in his environment.
Why choose the Banyan Security Platform?
- Easy to deploy and use – most folks can get the Banyan Security Platform – Team Edition up and running in 15 minutes or less, delivering an end-user experience that is superior to legacy VPNs and other forms of remote access.
- Actionable insights – Banyan offers actionable insights through deep visibility into the applications, services, users, devices, and activity that are present, which permits superior control and accountability.
- High security – the Banyan Security Platform is built on a foundation of zero trust principles that dramatically improve your organization’s security posture. These features include least privilege access, continuous authorization that leverages real-time device posture and trust, user trust, and resource sensitivity as defined in granular policy controls.
Speak with our Zero Trust experts about your security initiatives.
