
Ok, y’all, we are now in the middle of post-covid work environments where the freedom of location has been a selling point for companies that have remote positions. But this freedom pairs with the adage “with great power comes great responsibility,” where we are relying on our end users to police their own internet activity. Here’s where internet threat protection comes in.
From a security standpoint, this is a rather difficult problem; our biggest line of defense for malicious activity and compliance has been managing the thing that makes connection to the internet on employees devices function. And we already know from when we implemented these tools (what seems like eons ago): employees that felt unsupervised will sometimes do things with their devices like no one is watching; whether in ignorance, acting from defiance, or the ol’ DGAF, I will let you be the judge…
For those familiar with children and computers that are school property, you know the above sentiment all too well. Children will do almost anything to get to the corner of the internet that they are trying to view. They eventually land an arsenal of tools like VPNs, archival sites, and translation sites to avoid the intended class work and instead continue on in the Minecraft mission (or worse).
The Internet Threat Protection Problem
Possibly having witnessed this firsthand, you’ll recognize that our task is to manage the internet traffic that can come from a corporate device as best as we can while not annoying users with the controlled access point. Might I add, rightly so. As you find yourself in this problem of having to manage employees like they are middle schoolers with school computers.
The task for management is simple. Once upon a time, central management of internet traffic mostly worked (before the days of remote working as a standard). The trick is achieving the same kind of management of internet traffic that was once centralized, knowing we can no longer rely on that central choke point.
You start to ask “How do I do this to my employees without feeling like a principal at a school district?” After all, freedom of location includes this idea that you can achieve work without feeling like every move you make is being watched (mid-day laundry is such a nice break from the grind, right?).
Now, possibly you realize that the problem space is split in two related but distinct asks from the business. First is content management, the harbinger of dread as you take this on, and then there are malicious threats spread throughout the internet that even the most technically savvy individual could encounter without knowing. Furthermore, it’s becoming apparent that number 2 has a lot of surface area, as it’s not just spam and malware anymore. It’s botnets, ransomware, cryptoming, crypto schemes, dark generative AI, and so on that have blossomed as malicious actors are finding more creative ways to target users (cough cough wink wink read these other blogs on just that <link>).
Now What?
We have to find a way to protect our users from all these threats identified in ask two, while being very cautious to only apply what is strictly necessary to be in compliance with corporate policies on acceptable use (ask 1). Additionally, we need to make sure that:
- If end users are not doing anything harmful, that they aren’t even aware these protections are in place
- That any interference with web surfing and usage is minimal and rapid so that there is not a feeling of slowness or bad wifi service
- If in a state where protections need to be removed due to mis-categorization or impediment of work, it can be done easily and even the most tech illiterate person can fix their own issues.
How Banyan Does Internet Threat Protection
We felt that the best method to provide the best experience was to leave the heavy lifting to the DNS rather than the device. To emphasize, we decided early on that any protections and controls that were to be applied to the device when it’s surfing the web was to be done via our Global DNS servers rather than locally on the device. So that the speed was achieved and we only had to do simple management of the DNS provider on the machine, which is a time tested process.
Because the traffic is sent to our global DNS, we moved to provide a layer of validation to each DNS request, where configurations made by admins would be checked against the devices those configurations target, and a decision is made whether or not to supply the device with the resource it requested.
For the configurations, we purposefully called out the two asks that would come from the business. The admin has the ability to control which threats to block on a device (and which content to allow or block to adhere to the company’s corporate policy).
Internet Threat Protection, Step by Step
Start by defining which types of threats you deem not safe for your end users. We have several threat classifications: classic threats like malware (blue), modern threats like crypto mining (gray), ways in which a person could circumvent protection which we deem a threat (orange), and we have protections for websites that have statistically high chance to be malicious in some way but have yet to be evaluated by the industry (pink). Shown below is that breakdown:
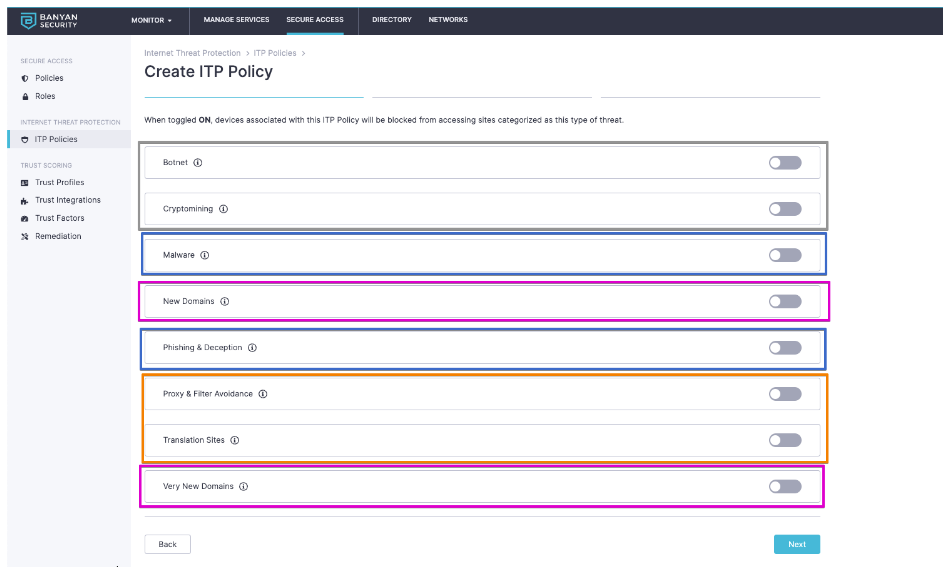
We recommend all threats should be enabled.
To comply with corporate compliance, we allow you to select from one of over 30+ categories to block traffic from. Furthermore, you can define specific sites you wish to allow (or not allow) your end users access to. For example, if you want to block social media from your corporate devices but still allow the end users access to LinkedIn, it’s as easy as entering LinkedIn’s domain and moving on. Banyan’s Internet Threat Protection has you covered:
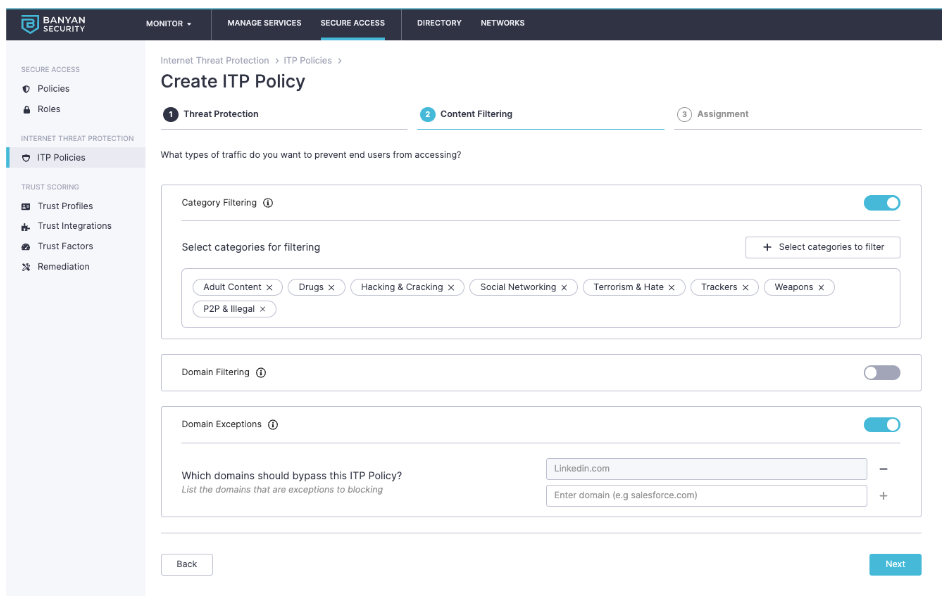
Every corporate policy is different; therefore, we will let you be the best judge for what content you wish to manage.
Lastly, we provide the finely-tuned targeting that exists today in Banyan. Being able to target based on a number of factors, such as MDM management, user group, platform, and ownership. This means you will have an easy way to exclude BYOD from any policy that blocks internet usage.
Additionally, we provide a way to message blocked individuals with instructions, giving them details on how they can engage you or your teams if they believe a block was inappropriately placed.
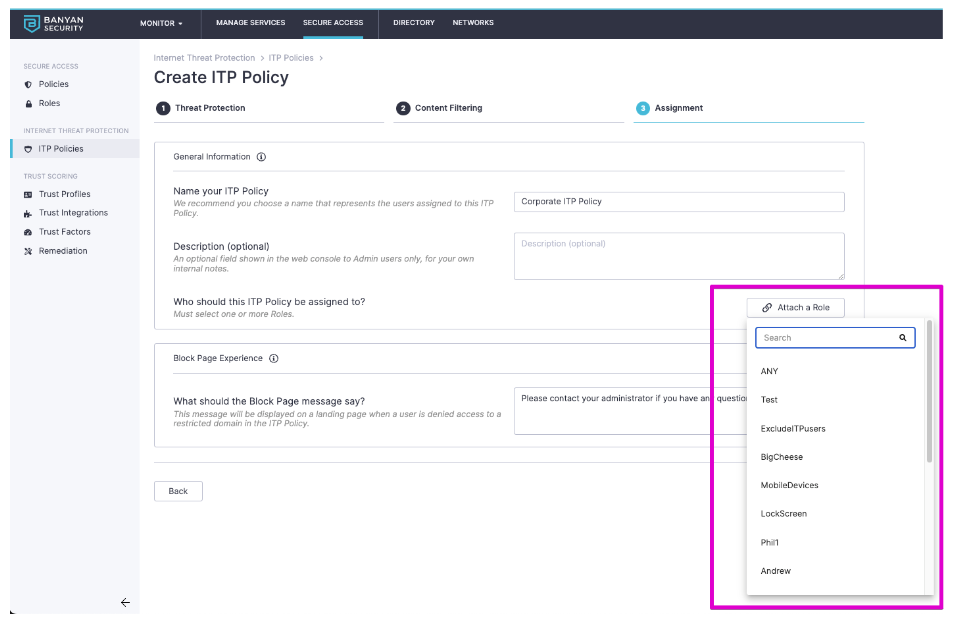
Once the policy is saved, the device will pick up the action to start routing DNS requests to Banyan within 15 minutes, leading to a simple and painless deployment.
Learn more about Banyan Internet Threat Protection (available in our Unlimited Solution) by setting up a custom demo with our team.



