Last year in 2022, there were 1,802 data compromises affecting more than 422 million people – but the LastPass data breach is the one that has security practitioners chatting. The original incident happened in August of 2022. Initially, we were told it was a “minor” breach…yet the story continues to evolve even at the time of the writing of this blog. One of the more significant factors: how LastPass places the blame for the breach on remote working (instead of on how they implemented their own remote working security policies). It’s a decision that’s left many in the industry scratching their heads, while at the same time seeking ways to prevent the same attacks in their own companies.
Unpacking the LastPass Breach
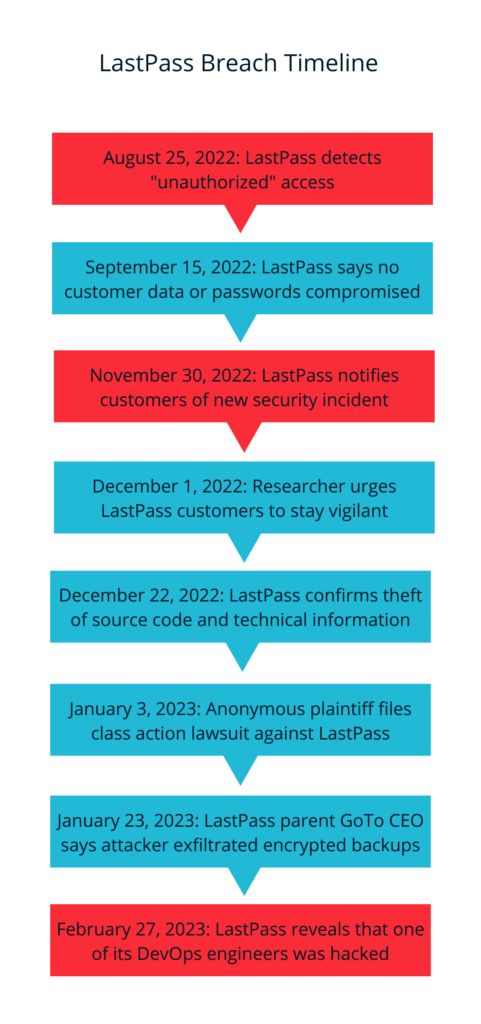
Let’s start at the beginning of the disclosures: on Dec. 22, LastPass CEO Karim Toubba acknowledged in a blog post that the August 2022 security incident directly paved the way for an “unauthorized party” to steal customer account information and sensitive vault data.
GoTo (the company formerly known as LogMeIn that acquired LastPass in 2021), released a March 1 2023 statement regarding the original security breach it experienced back in August 2022. GoTo has 800,000 enterprise and private users, but the company is still refusing to disclose how many of them were affected by the LastPass breach. LastPass is said to have a registered user base of over 25 million.
As more information came out, LastPass confirmed that a threat actor had “targeted a senior DevOps engineer by exploiting vulnerable third-party software.” The third-party software was the popular media streaming software Plex…and the vulnerability was a two-year old CVE from 2020.
What Was Lost
As detailed in the incident summaries, the threat actor stole both LastPass proprietary data and customer data, including the following:
Summary of Data Accessed in Incident 1:
- On-demand, cloud-based development and source code repositories – this included 14 of 200 software repositories.
- Internal scripts from the repositories – these contained LastPass secrets and certificates.
- Internal documentation – technical information that described how the development environment operated.
Summary of Data Accessed in Incident 2:
- DevOps Secrets – restricted secrets that were used to gain access to our cloud-based backup storage.
- Cloud-based backup storage – contained configuration data, API secrets, third-party integration secrets, customer metadata, and backups of all customer vault data. All sensitive customer vault data, other than URLs, file paths to installed LastPass Windows or macOS software, and certain use cases involving email addresses, were encrypted using the LastPass Zero knowledge model and could only be decrypted with a unique encryption key derived from each user’s master password. End-user master passwords are never known to LastPass and are not stored or maintained by LastPass – therefore, they were not included in the exfiltrated data.
- Backup of LastPass MFA/Federation Database – contained copies of LastPass Authenticator seeds, telephone numbers used for the MFA backup option (if enabled), as well as a split knowledge component (the K2 “key”) used for LastPass federation (if enabled). This database was encrypted, but the separately-stored decryption key was included in the secrets stolen by the threat actor during the second incident.
The scary details are here https://support.lastpass.com/help/what-data-was-accessed; a quick glance shows how much data was accessed.
If you’re one of the 25 million people potentially affected by the LastPass data breach, our advice is below.
Next Steps for Consumer LastPass Subscribers:
- Patch, upgrade, and disable network adapters, or get rid of anything on your home network that may be compromised. If a device in your home is not long supported (end of life) and not getting software updates, it’s time to take it offline.
- Find a new password manager. Given LastPass’ history with security incidents and considering the severity of this latest breach, now is a better time than ever to seek an alternative.
- Change your most important site-level passwords immediately. This includes passwords for anything like online banking, financial records, internal company logins and medical information. Make sure these new passwords are strong and unique.
- Change your other online passwords, especially if they were stored in LastPass. Start with the order of importance, changing the passwords to accounts like email and social media profiles, then you can start moving to other accounts that may not be as critical.
- Enable two-factor authentication wherever possible. Once you’ve changed your passwords, make sure to enable 2FA on any online account that offers it. This will give you an added layer of protection by alerting you and requiring you to authorize each login attempt. That means even if someone ends up obtaining your new password, they shouldn’t be able to gain access to a given site without your secondary authenticating device (typically your phone).
- Change your master password. For those of you who are brave and loyal to LastPass, do this fast. Though this doesn’t change the threat level to the stolen vaults, it’s still prudent to help mitigate the threats of any potential future attack.
Next Steps for Organizations Using LastPass:
- Ensure that network and application segmentation is enabled, and that lateral movement is reduced.
- Patch all internal and infrastructure resources to help reduce the risk of systems with known vulnerabilities being discovered and compromised.
- Deploy Endpoint Detection and Response (EDR) and other security software to all systems that will be granted access.
- Ensure that end user systems are upgraded so get all, new security fixes.
- Scan end user devices for software that isn’t corporate approved.
- Enable device posture assessments like those done by Banyan Security’s Device Trust. Create a policy that instantly revokes or reduces authorization when a device goes out of compliance.
- Enable User and Entity Behavior Analytics (UEBA) to discover unexpected and/or unwanted behavior from known users and devices.
- Enable tunnel traffic discovery and analysis to further gain insights into suspicious traffic patterns, sources, and/or destinations.
- Enable application and server discovery to find systems on-premises or in the cloud that may be unknown, unpatched, or misconfigured.
What Now?
From the lens of another security company in the industry: the choice LastPass made to place blame at the feet of the remote worker (and on the lack of security in remote working) has inherent problems. The LastPass stance is a complicated one, given how broad the remote worker migration has been, particularly over the past five years. Many companies have built reputations on securing employees no matter where they happen to be sitting. One thing is for sure: remote working is here to stay, and it’s far less painful to secure your workforce before the breach than to risk losing your company afterward.



