By now, you’ve surely heard about some of the breaches that have been happening when company A gets illegally accessed via threat actors hacking into one of company A’s vendors. Microsoft was breached when hackers got into SolarWinds. Twilio was recently breached when hackers were able to hack Okta. Learn more about what exactly happened, check out this great article Okta one-time MFA passcodes exposed in Twilio cyberattack. The list of these types of indirect breaches is long and continues to grow. The bad news for vendors like Okta is that it’s happened more than once this year. Can it have been prevented?

Figure 1: MFA is not enough!
Before we look at how Banyan Security can enhance MFA and prevent these types of attacks, let’s take a quick look at history. User security started with credentials: a username name and a password. Passwords were never good enough and lots of folks kept them as defaults or on post-it notes on their computers. Multi-factor authentication (MFA) and one-time passwords (OTP) came along and tried to correct some of these issues. They’ve done a good job, but we know about the limitations. Moreover, the identity systems such as Microsoft Active Directory or token-based systems from RSA and the likes of Google Authenticator used to sit behind a firewall and VPN. These systems have evolved into SaaS solutions. Folks are using Microsoft Azure AD, Okta, OneLogin, and Ping which are public-facing SaaS services making it easy for attackers to figure out who is using what. Try typing <any company name>.okta.com and you’ll likely find a resulting page for that company confirming that they are using Okta for identity. No more secrets hidden behind VPNs.
Identity has become the weakest link and attackers are using new methods to phish for credentials. One example of this is domain squatting. In the latest Twilio attack, attackers registered the twilio-sso.com and twilio-okta.com domain names at registrar Porkbun, and created phishing sites for them. They then sent messages to users hoping one, just one, would respond. Unfortunately for Twilio, the domains seemed legit enough to their employees and the attack worked.

Figure 2: MFA phishing
As incredible as it may seem, the days of using an authentication strategy built on something you have, something you know, and an inherence factor are likely behind us. MFA phishing attacks are now the norm and standard IAM practices are no longer sufficient to protect access and authorization to mission critical resources. MFA can be better.
How Banyan enhances MFA
Simply stated, factoring user and device identity and trust into the equation could have prevented the attacks. Let’s learn how.
Banyan Security’s ZTNA solution integrates with leading MFA vendors. These MFA vendors can be configured to use certificate-based authentication aka cert-auth. These intelligent certificates tie the device to the user. Without them, no access will even be considered. Once the user is identified, the device identity and posture assessment process is completed to generate a Banyan TrustScore. User identity, including MFA, or device identity and trust alone are never enough to get access.
To summarize, before any access is granted, the following must be true:
- Banyan must trust the specific MFA vendor
- Banyan must deploy the Banyan app to a very specific end user device
- Banyan must authenticate the user and ensure that they can enroll their specific end user device
- Banyan must generate an intelligent certificate for that specific user and specific device
- Banyan must check the identity and authorization level of the user
- Banyan must, in a timely matter, validate a component of the user identity with the MFA vendor
- Banyan must check the identity and authorization level of the device
- Banyan must check the posture level of the device
- Banyan must check the configured risk tolerance of the resource
This is a secure, defense-in-depth multi-step process. If any step is skipped, no access is granted! Luckily for end users, most of this magic happens behind the scenes so ensure your users aren’t jumping through hoops to get secure access.
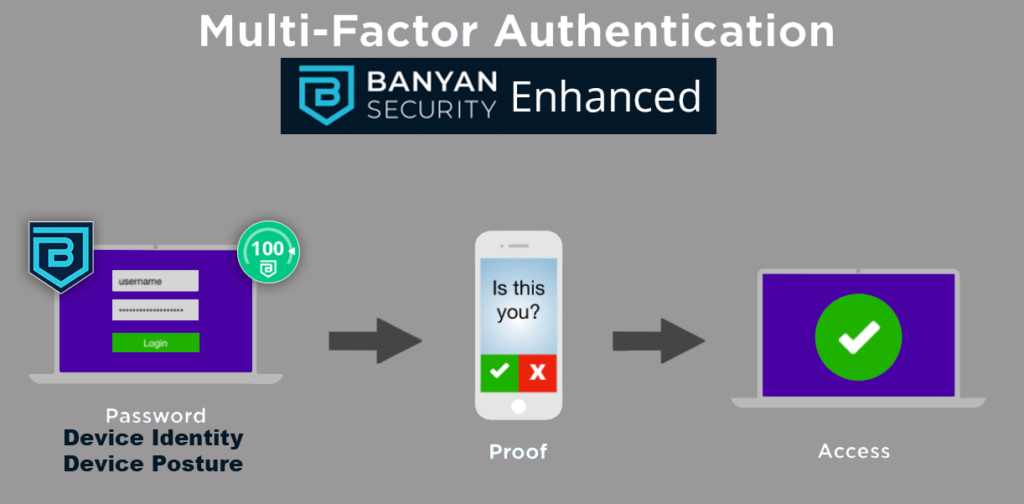
Figure 3: Banyan-enhanced MFA
You may be thinking, if the attacker has credentials and has phished MFA, they can enroll a new device and gain access. With Banyan’s ZTNA solution, new device enrollment can be blocked by rotating invite codes, or completely disabling the process and leveraging Unified Endpoint Management (UEM) to push out the Banyan app along with the intelligent certificate.
Banyan’s ZTNA granular policies also ensure that applications can only be accessed by devices with a known and specific identity and posture. Unknown and unauthorized devices are banned from attempting enrollment and access.
Banyan’s latest offering further enhances MFA
Banyan’s expansion into Security Service Edge (SSE) comes as customers are looking for innovative solutions to problems such as the domain squatting mentioned above. Banyan introduced DNS Threat Detection, which provide acceptable use policy along with malicious domain protection. Moreover, Banyan’s DNS Threat Detection blocks newly registered domains which are often set up using shady registrars anonymously and within hours or days of the attack.
Update – I’ve also recorded a quick video on using ZTNA to complement your MFA strategy.



