In 2020 we saw organizations across all industries forced to quickly scale up existing security tools to handle the near-overnight increase of remote workers resulting from the global pandemic. There was insufficient time available to evaluate architectures and figure out how to make sure remote access happened securely at scale. More often than not, organizations simply bought a lot more of whatever they already had.
2021 – The Year of the Modern Security
According to Chinese zodiac, 2021 is technically the Year of the Ox. Oxen are considered hard workers in the background, intelligent and reliable, but never demanding praise. Sounds similar to the life of an IT or Security professional! Supporting the work from anywhere reality over the course of a few months was a tremendous feat and everyone involved should be applauded. Now lies ahead a larger opportunity for the industry – shifting to modern security architectures and incorporating Zero Trust principles.
As we begin 2021, security leaders are starting to have a chance to breathe and assess the myriad of available Zero Trust tools so they can make investment decisions for their organization as well as their own products. From our experience in helping customers meet their security goals, we have seen that end user experience and buy-in is instrumental to successful Zero Trust implementations. Selecting solutions that prioritize user experience leads to IT and Security becoming company heroes. Ultimately this leads to receiving more praise than an ox could ever ask for!
Simplifying End User Onboarding and Access
One of our main product goals this year involves enhancing onboarding experiences. Historically, increased security always results in trading off end user experiences. Whether it be requiring RSA fobs for certain networks or installing agents to access certain resources, the end user usually bears the brunt of the impact. A Zero Trust architecture actually has the potential to change this. Here are some example initiatives that move the needle towards Zero Trust:
1) Ditching the VPN
A shift towards Zero Trust involves moving away from a trusted network model, and therefore reducing the reliance on a VPN for access controls. By leveraging modern remote access solutions, organizations have visibility into how resources are being accessed, gain the ability to assign least-privilege access, and no longer have a single choke point in their architecture.
Banyan has an intelligent aware proxy that lets organizations replace their VPN with no network changes while still owning their data plane.
End User benefits include:
- Not having to worry about when and how to authenticate to the VPN. Many VPNs do not have integrations into identity providers
- Eliminates clunky VPN clients that decrease battery life and degrade performance
2) Acceptance of BYOD
“Never Trust, Always Verify” makes room for a surge in BYOD use cases. As long as the user and device security posture can be validated, then application access decisions don’t need to factor in if the device is owned by the organization or the end user. Forcing users to enroll into Unified Endpoint Management (UEM) tools to push Wi-Fi or VPN profiles to connect to restricted networks is a solution of the past.
End user benefits include:
- Protects users privacy by segmenting work and personal data on the same device
- Not having to carry multiple phones or laptops
3) Rise of Passwordless and SSO
Zero Trust products have helped drive an increase of SSO within organizations. This has strongly increased employee productivity and experience. At the same time, the global passwordless market is set to reach $450B by 2030. This allows the end users to leverage something they have (Yubikey, mobile device) and/or something they are (facial identification, retina scan) to access their applications.
End user benefits:
- Increase of productivity by using single sign on
- Fewer lockouts due to forgotten passwords
The end state of Zero Trust has compelling benefits but what’s less discussed is the end user journey to get there.
Do end users have to download other clients that are equally user unfriendly?
Do they have to go through dozens of frightening prompts and steps to register to a UEM tool for obtaining certificates?
The Need for Device Trust
At Banyan, we have built-in integrations with Identity Providers that are responsible for authenticating the user. Once we validate who the user is we can ensure the right user has the right access to the right resource. This functionality extends to all infrastructure services, hosted websites, and SaaS applications secured by Banyan. However, a Zero Trust architecture cannot be reached without evaluating device trust.
The first step in an organization’s Zero Trust journey should be to ensure they have an understanding of their users and devices. Identity-centric tools excel at user authentication but offload device posture checks to UEM tools. UEM tools can evaluate device compliance policies but often fall flat when it comes to BYOD and Third party access use cases.
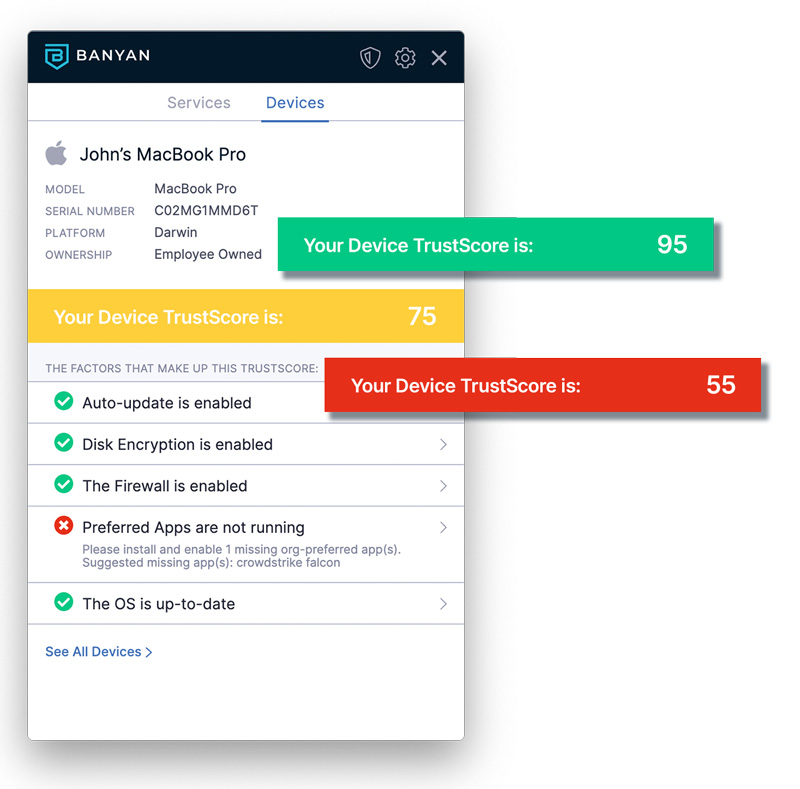
Banyan’s Zero Trust Remote Access Platform takes signals from existing IDP, UEM, and EDR tools as well as the device and incorporates them into a comprehensive Device Trust Score. The same score is used in authorization decisions to all application types and if a device has a low Trust Score, Banyan can immediately cut off access to the resource. Device trust is calculated across all major platforms and ownership types making it easy to extend to various use cases within an organization. But none of this matters if it requires end users having to move boulders to achieve…
Introducing Zero Touch Deployment
Our most recent step towards simplifying end user experience is focused on the Banyan desktop app installation and registration. We have streamlined the workflow in a way that helps customers answer a critical first question in their Zero Trust journey:
How do I obtain the trust level of devices in my organization?
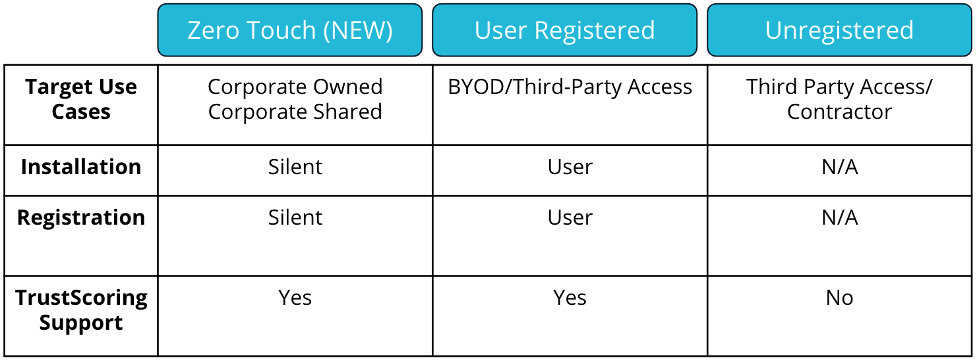
(Modes for deploying and registering devices)
Banyan’s Zero Touch Deployment is a completely silent way of installing and registering devices with Banyan that prioritizes the end user’s experience. It is a winning deployment method for IT because organizations can now see the trust scores of their device fleet prior to fine tuning policies and configuring least-privilege access to resources. IT teams never want to be surprised by the impact of a policy change so now this impact can be planned for.
Zero Touch mode is the recommended method of deploying the Banyan desktop app when a Device Manager is being used. For BYOD use cases, Banyan user registration boils down to simply installing the app (https://getbanyan.app) and signing in with your organization’s Identity Provider. No profiles. No requests for broad permissions. No calls to IT Support.
See Banyan’s End User Experience Today
All the benefits discussed above are all available today within the Banyan product. We are looking forward to sharing more end user experience focused initiatives in future releases. To leverage Banyan’s Zero Touch Deployment, review our docs for specific steps depending on your UEM tool. Better yet, reach out and let us demo our end user experiences for you!



