Imagine a world where access to sensitive corporate data is not granted based on just a corporate users’ credentials, but rather on the business sensitivity of the APIs/data they’re accessing, their typical access patterns, the vulnerability of the application and infrastructure providing access, the security profile of the location they’re accessing from, the real-time security posture of the device they’re using, and a hundred other factors that guarantees the absolute least privileged access to data, all without any human intervention.
To make this vision a reality, we introduce a powerful concept called Banyan TrustScore, a fundamental building block for creating such a system. This score is analogous to the credit scores that are widely used in the financial industry as the foundation to measure creditworthiness. This article describes the secure access challenges faced by enterprises today and how the Banyan TrustScore helps alleviate them.

Credit Score captures your creditworthiness
Worker mobility and Multi-cloud are the new mantras
Today’s enterprises have embraced a highly dynamic workforce and geographically distributed applications and services for speed of delivery and cost efficiency reasons. However, this shift has made it extremely difficult to safeguard sensitive corporate data using traditional perimeter-based approaches to security using legacy tools such as VPNs and firewalls.
The workforce is no longer confined to employees working from office buildings – according to recent data the number of “loosely-coupled users” of enterprises such as contractors, partners, vendors, suppliers, etc. often exceeds even the total number of employees in the company. Furthermore, these users are accessing corporate data from their personal BYOD devices such as mobile phones and laptops, and from insecure locations such as coffee-shops and airplanes.
The applications and services exposing corporate data are also no longer confined to data centers running simple monolithic applications. Today’s applications are spread across multiple clouds (e.g., AWS, Azure, GCP), various regions (e.g., U.S.-East, Europe, Asia), and are built using different architectures (e.g., Kubernetes/microservices, three-tier). Finally, the consumers of the APIs exposed by applications are not only users, but increasingly other applications and microservices.
Establishing trust for secure access has become a major problem
These trends have resulted in several challenges listed below for securing access to corporate data – the common theme is the inability to accurately attest to the trustworthiness of the requestor for allowing or denying access to sensitive corporate data.
1) A slew of access-related data-breaches
We see multiple data breaches every day, with, on average, more than 6M records lost or stolen per day. Lacking access controls is one of the most dominant causes for these breaches. These data clearly show that existing perimeter-based approaches that rely on just authentication (e.g., MFA) and network factors (e.g., IP addresses, network segments) are fundamentally insufficient to protect corporate data. To close this chasm, tens to hundreds of additional factors across users, devices, applications, and infrastructure need to be taken into account to guard access to sensitive corporate data.
2) Role and policy proliferation
Security administrators have resigned themselves to specifying many roles and policies across different security tools to manage different levels of corporate access. This approach is not just time-consuming and complex, but also very error-prone and can open gaping security holes in enterprises’ overall access posture.
3) Security tools galore
In 2020, the average enterprise deployed more than 76 security tools. A significant jump from 2018 and 2019 numbers when enterprises were deploying at least 45 tools on average. These disparate tools span several aspects of security such as network security (VPNs, firewalls), application security (WAFs, vulnerability management), user identity management (IAM), endpoint security (EDRs) and device management (MDMs). Although several such tools should affect access decisions for sensitive corporate resources, they are deployed in their own silos and it’s very difficult to bring them together to make real-time access decisions.
4) Overburdened security administrators
Relatively small security teams are responsible for managing the entire corporate infrastructure. In addition to managing tens of security tools and supporting potentially insecure BYOD devices, they are also responsible for ensuring employees have secure access to their corporate data and are on the hook to immediately fix any issue that could cause a breach or affect employee productivity.
Recent attempts to solve this problem have focused on providing conditional or contextual access by combining user and device factors to provide a more secure authentication. But unfortunately, these “bigger padlock on the front-door” approaches address only a small part of the problem and leave behind gaping security holes. Most of the data breaches today are due to insider threats that are post-login: privilege escalation/abuse, token reuse, misconfigured and exposed servers, and vulnerable applications/APIs are a few examples of access-related threats that are just not addressed by such frameworks.
Furthermore, most security tools operate in silos today, making it very complicated to bring them together in an intuitive and easily consumable way to make access decisions. For example, typical enterprises deploy several security tools related to identity (IDPs), devices (MDMs, EDRs), networks (firewalls, IPS/IDS), infrastructure (vulnerability scanners), applications (WAFs), etc. Most of them have a direct or indirect impact on allowing access to sensitive corporate data. Capturing signals from all these sources in real-time is a huge undertaking that enterprises don’t have the time or expertise to pull off today.
Banyan TrustScore quantifies Confidence in the Zero Trust Era
To overcome these challenges, we have developed a concept called Banyan TrustScore to quantify the level of trust to attribute to accessing principals, whether they are users, devices, or client applications. Just like a credit score in the financial industry indicates how trustworthy the user is so that banks can approve loans, issue credit cards, etc., the TrustScore indicates how trustworthy the user, device, and client applications are so that our platform can make access decisions to a company’s sensitive resources.
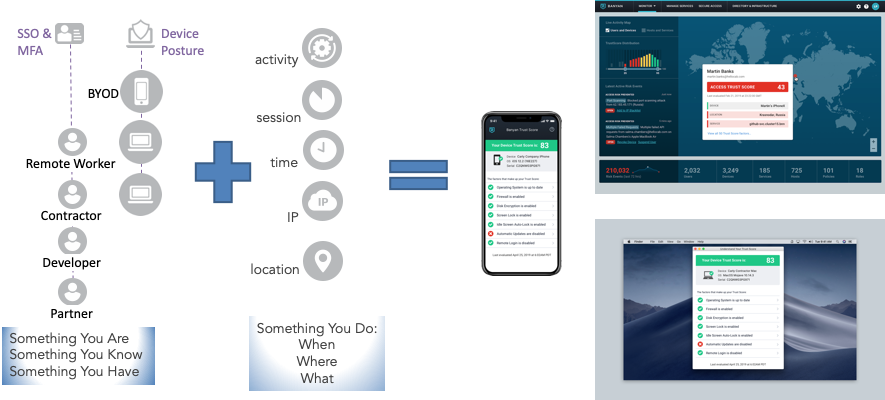
Example of a Banyan TrustScore combining a variety of factors
Banyan TrustScore enables continuous authorization to sensitive corporate resources and APIs, and goes well beyond just coarse-grain login/authentication decisions. The TrustScore is computed in real-time using machine-learning based on hundreds of user, device, infrastructure, network, and application factors collected from both our sensors and tens of other security tools already deployed in enterprise environments (e.g., IDPs, firewalls, SIEMs, EDRs, MDMs, etc.). This enables companies to leverage the investment they’ve already made in other security tools to also contribute to access decisions and improve the overall security posture. For example, if an EDR tool detects that a device has been compromised due to a zero-day attack, that information immediately affects the TrustScore and any access from that device to sensitive data is immediately blocked.
This score also enables security administrators to easily write policies that provide differentiated, least privileged access to users based on the sensitivity of data they’re accessing. The same role can grant different levels of access based on the TrustScore, thereby avoiding role proliferation. For example, a developer can both write and administer Confluence from home or a coffee shop that she frequents, but can be allowed to only read with no administrative privileges when accessing from an airplane – all with just one policy and one role.
Exposing the TrustScore to users also provides an intuitive way for the company workforce to check their and their device’s security posture and improve it on their own. This enables employees to work in concert with the security teams, thereby reducing their burden and creating a safer corporate environment. For example, if an employee is denied access, they can easily check that this is because their TrustScore is low for not applying the latest critical patch for their laptop. The employee can quickly patch the laptop and gain access without needing any intervention from the security administrator.
Paving the way for a Continuous Zero Trust Platform
To summarize, the Banyan TrustScore is a fundamental building block to create a platform that continuously evolves to provide least privilege access to sensitive corporate data – what we call Banyan Continuous Zero Trust platform. Our customers are already seeing huge benefits by deploying this in their environments. We are very excited to open it up it to the rest of the world. Please schedule a demo to get started today!



