
Device trust? Geek-speak for “how safe is your device,” device trust is foundational to the security of an organization and its users. As a counterpoint, there’s device shame: you don’t want to be the one to introduce a problem into the organization. Also, for most users, the computer they use for work also has a lot of personal information or files on it, for example, family pictures and other documents that were downloaded during the course of the workday. Having a device with low trust levels looks like this: any place you visit, and then access the network is a nexus from which serious issues can spread. And with the right amount of logging and forensic information, this activity can be traced back to you. This is why having a trusted device is the cornerstone to a robust security strategy.
To give you an idea of scale of the global problem with low trust levels, statistics suggest up to 900 million unpatched Windows machines with vulnerabilities that can possibly be breached. Also, just on Android, over 550 vulnerabilities were found in 2021, and malware was present on over 10 million mobile devices (including iOS). Finally, according to Ironscales’ State of Cybersecurity Survey, phishing emails have become more frequent. Since the start of the pandemic in 2020, 81% of global organizations have reported more email phishing attacks. So what can be done and why do end users care?
Looking at the below Banyan app we can see there are a few things that we calculate our trust levels on. There are more factors than the below but in this blog we’ll just look at what Banyan looks at directly and the types of information that we can get from some of our EDR partners such as Crowdstrike and SentinelOne.
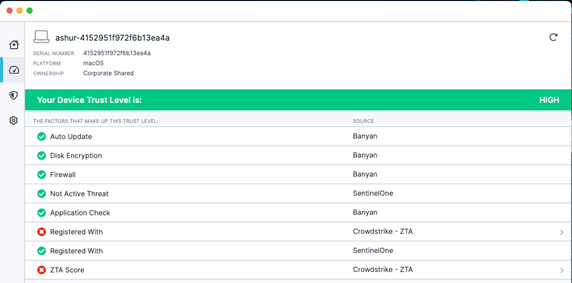
The four standard Banyan App factors include:
1. Auto Update
Ensures that the end user device is always running the latest and greatest operating systems which includes security updates.
2. Disk Encryption
Ensure that disk encryption is configured to help protect any intellectual property (IP) that is on the device in case the device is stolen or lost.
3. Firewall
Ensures that on-device software firewall is configured. The default configuration for the firewall usually includes blocking all inbound connections as well as blocking ICMP replies which are used for ping tests looking for systems to attack. This will also keep the system details invisible from Nmap and other scans.
4.Application Check
Ensures that the required, corporate-issued security software is installed and running, along will checking for undesired or malicious software that is installed. Some software, such as Metasploit, may be used by bad actors doing bad things, or penetration testers checking system security. Many times, these get flagged, and administrators need to whitelist systems that have a reason to have these types of software.
More factors as well EDR integrations are available and can be configured, either in visibility or enforcement mode.
Endpoint Detection and Response (EDR) integrations are important. The typical use case is that the EDR agent is installed on an end user device, a policy is configured on the EDR, and a score or compliance state is sent to the SSE/ZTNA solution. This is similar with MDM/UEM. How this score or compliance state is calculated depends on the vendor. These integrations are quickly configured using an API URL and a token for authentication.
SentinelOne sends over information about agent installation and state as well as flagging for active threats. Remediation can happen using instructions along with functionality built into the SentinelOne app such as the quarantine of malicious files.
The Crowdstrike Zero Trust Assessment (ZTA) delivers real-time security posture assessments across all endpoints regardless of location, network, and user. Falcon ZTA enables enforcement of dynamic conditional access based on device health and compliance checks that mitigate the risk to users and the organization. Every endpoint is granted least privileged access and is assessed before gaining access to sensitive data and corporate assets – ensuring Zero Trust enforcement across all endpoints. By expanding Zero Trust beyond authentication and including device security, CrowdStrike Falcon ZTA helps organizations maintain a holistic cybersecurity approach that protects their data and users from the sophisticated tactics of cyber adversaries.
With the recently announced acquisition of Preempt Security, CrowdStrike has advanced its Zero Trust capabilities to achieve end-to-end, real-time visibility and granular enforcement with advanced conditional access technology for real-time access control and threat prevention. The new capabilities will help unify identity and workload-centric conditional access capabilities with the CrowdStrike Falcon protection suite to help secure users, workloads, and data, regardless of location and network and without modification to existing legacy infrastructure and operating systems.
To learn more about how Banyan ensures device trust for your network, attend our weekly live demo or schedule a custom demo today.



