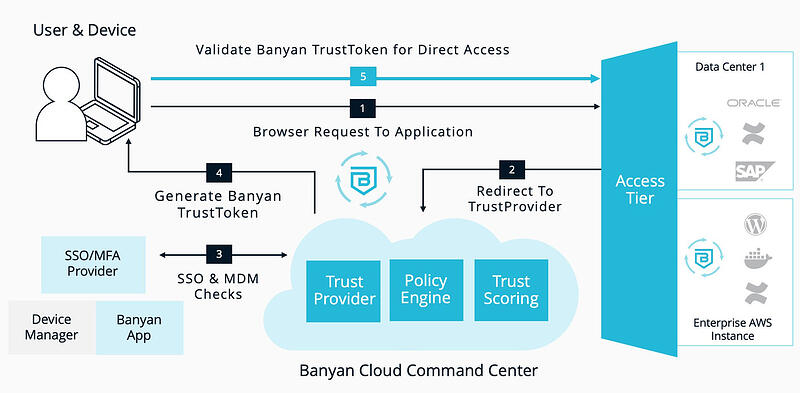
Legacy VPN Replacement
75% of enterprises today are in some form of hybrid cloud deployment. Providing a seamless remote access solution that traverses this complex environment is a huge IT and security challenge.The Problem
As enterprises progress on their digital transformation journey, they must enable secure remote access across their on-premises and cloud deployments. Network-centric solutions like traditional VPNs (Virtual Private Networks) are not designed to meet modern organizations’ scale, performance, and usability needs, especially with complex hybrid cloud environments.

Management Complexity
- No centralized way to secure IaaS, on-premises, and SaaS applications especially if applications can move across clouds.
- Complex network-level policies to segment access, which have to be constantly updated to match dynamic user and application environments.

Massive Security Gap
- Legacy VPN solutions grant full access to network resources, allowing malicious actors with VPN access to move laterally across the corporate ecosystem.
- One-time authentication approaches fail to provide real-time detection or enforcement of detected abnormal activity.

Poor Performance & Scale
- Due to deployment complexity, users experience performance delays and are often unable to access applications due to VPN connectivity issues.
- VPNs can be very expensive to acquire, maintain, and upgrade.
Improved Security Posture
- Own your data plane and provide differentiated access based on user, device, and other relevant attributes
- Integrate with your existing PKI infrastructure / CAs to completely control the confidentiality and privacy of your data

Massive Management Simplicity
- Homogeneous experience whether servers are deployed in IaaS or on-premises
- Simplified experience whether IaaS, on-premises, or SaaS applications using our as-a-service Banyan offering

Seamless & Fast User Experience
- Direct access to servers deployed on private clouds or Infrastructure as a Service (IaaS)
- Supports general TCP protocols like MySQL
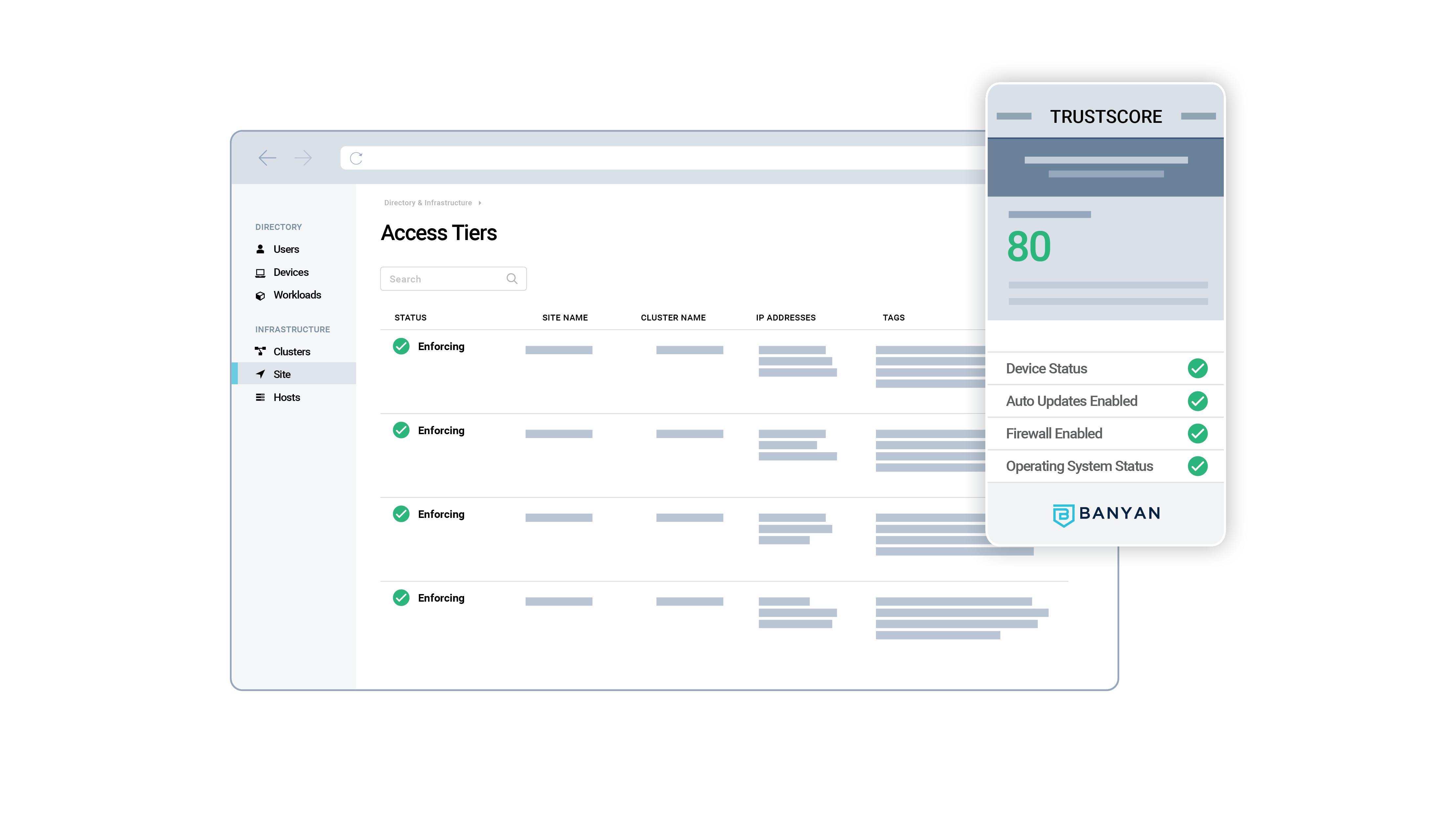
Key Features for VPN Replacement
- Integrate with your cloud infrastructure in AWS, Azure, GCP, or VMware and leverage their auto-scaling load balancers and DDoS protection systems
- Write human-readable policies for differentiated access leveraging easy-to-use templates. Underneath the hood, a hybrid RBAC/ABAC system allows you to write highly custom policies, if needed
- Passwordless access to application/servers