Remote Access VPNs have been around for over 20 years. Having worked in this space for a long time, I know the early evolution was fast. We went from dedicated concentrators to beefier appliances with crypto accelerators to integrated functionality in next-generation firewalls (NGFW) running custom ASICs (application-specific integrated circuits). Then the evolution seemed to slow down. Customers said, “it just worked” and that’s when things got scary. Using custom tools, we found thousands of appliances from all vendors that no longer had support, were already deemed End-of-Life (EoL), or were just not being updated anymore. The ”it just works” mentality means a lot of different things depending on who you asked, but for most, it meant that employees were able to get on the network without any issues. The Remote Access VPN was seen as an access appliance and not a security appliance. This was exactly what attackers wanted. In 2019 alone, over 17,000 CVEs (Common Vulnerabilities and Exposures) were detected and of those over 4,000 were high severity. The National Vulnerability Database has an up-to-date catalog of them all.
Also, most of these remote access VPNs rely on open-source libraries like OpenSSL which are regularly found to have new types of software weaknesses (known as CWEs) and known vulnerabilities (known as CVEs). Updating and testing these libraries takes time and some vendors spend months trying to address issues only to be ignored by customers that either don’t think anything will happen to them or stopped paying for support. Vendors even offered free upgrades for high-risk vulnerabilities but this still made little impact.
With that in mind, we’ll take a quick look at why many of the remote access VPNs that you’ve used may have already been hacked.
Finding public-facing VPN devices is easy
In studies conducted by Banyan Security, we were able to easily find public-facing VPN devices for most companies across all industries in the Fortune 1000. 60% of organizations are using a common hostname. Our study analyzed over 150 common hostnames and then searched based on these for leading VPN/NGFW providers including Cisco, Palo Alto Networks, OpenVPN, Pulse Secure, and more. We also looked for Virtual Desktop Infrastructure (VDI) vendors like Citrix and VMware.
The industry with the most easily found VPN devices is higher education. They typically use vpn.<domain> or remote.<domain>. Moreover, most higher education organizations put instructions online.
While DNS scraping is still a possibility, it is recommended to not use common hostnames and put all instructions in a private portal that requires some level of authentication to access. Attackers are all about doing the most economical thing to gain access. These easy fixes will make your organization less attractive to them.
Finding out how and what to attack is easy
Legacy VPNs typically sit behind a firewall. The firewall is doing Network Address Translation (NAT) from an external IP address to an internal one. The firewall is also opening ports to allow inbound and outbound connections for VPN connectivity. Typically, ports 80 and 443 are opened. In some cases, port 500 is opened for IKE and port 4500 for IPSec are also opened. These ports may be opened for both UDP and TCP protocols. For organizations that allow SSH inbound, port 22 may also be available.
A free and simple tool such as Nmap can be used to find open ports on local and remote systems.
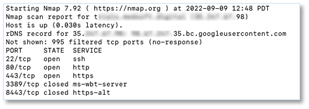
In this example, we googled “vpn edu” and the first result was from The University of Minnesota Duluth which is using Cisco AnyConnect on an ASA. As you can see, the hostname is vpn.d.umn.edu. A simple scan shows that ports 80 and 443 are open.
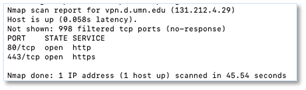
Solutions that use outbound only connections and protocols like SPA (single packet authorization) help alleviate this problem by hiding the system and not providing an attacker with another lead to pursue. We often refer to this as reducing the attack surface.
Getting free tools to compromise an appliance is easy
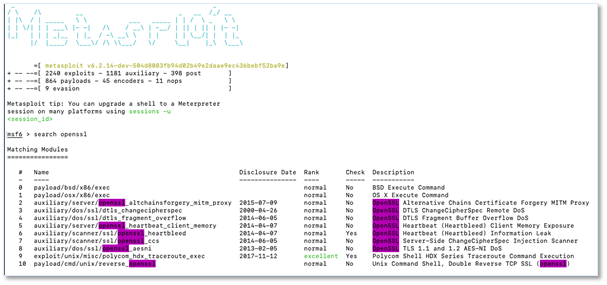
Now that you know which ports are available, free tools such as Metasploit and Kali Linux can be used. These two are specifically used for penetration testing (pentest) by the good guys but are also available to be used for more nefarious reasons.
Below is a sample of 10 exploits of OpenSSL. There are over 2,200 known exploits that can be used against systems that are exposed or haven’t been upgraded.
What now?
It’s easy to see that finding an edge device to compromise isn’t hard. Knowing some best practices for how to properly deploy and working with a security-focused vendor to upgrade your legacy VPN is key. Most organizations have recognized that adopting a zero trust security strategy is the best path forward. Zero trust network access (ZTNA) is a solution category that has emerged to address these issues. Banyan Security as an organization is all about providing the best administrator and end user experience while ensuring the highest level of security possible. Banyan Security’s ZTNA is a SaaS solution answers this call, drastically reducing the attack surface, and is upgraded often for every client to ensure that vulnerabilities are addressed quickly, for everyone.
To learn more about how Banyan Security can help you migrate away from your legacy VPN, visit www.banyansecurity.io



