Each year, parents assemble a backpack chock full of all the stuff kids need to return to school and be successful. Required books, pens, pencils, pencil box, ruled notebooks, lunchbox (with lunch! ;-)), extra jacket/hoodie, hat, etc. Obviously the content varies depending on their age, but the process is pretty consistent.
Now, as I think about it, lots of folks are busy trying to figure out how to help their organization adopt a zero trust strategy. Many are concerned about cost and budgets. Others worry about how long it might take. And we know that some are having difficulty figuring out where to start. Who to trust. When I say “we know”, I really mean it. Banyan Security just finished up working on a zero trust network access (ZTNA) study with noted research firm Sapio to learn where people are in the process. What are their motivations, how committed are they, where are the speed bumps that prevent them from stepping on the gas pedal.
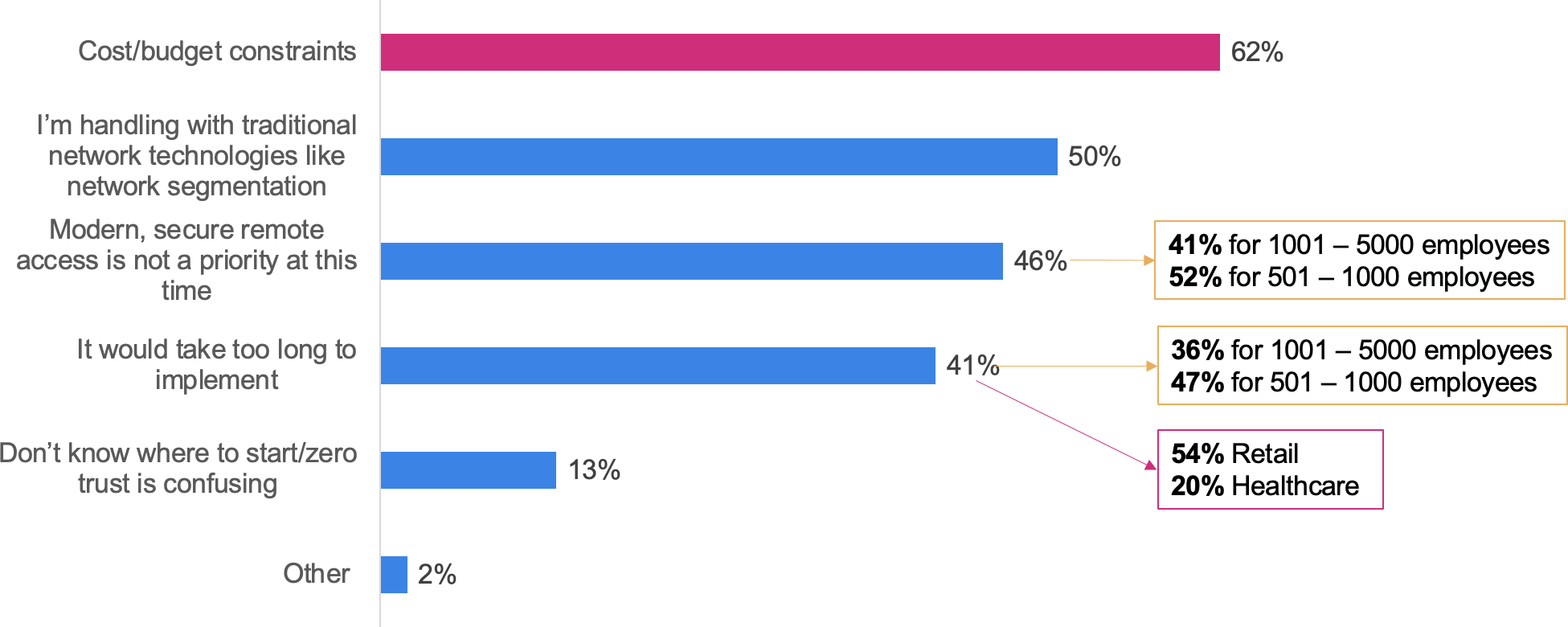
Cost and budget concerns are real. After all, we all have to live within our means. Contrary to what you might think, having access to the industry’s best ZTNA implementation isn’t expensive. In fact, you can literally get started for free. That’s right, zero dollars. It’s not some time-based demo, either. Banyan Security will give you a version of our Zero trust Remote Access product that supports teams of up to 20 people. And by the way, unlike some vendors, our enterprise offering has no hidden per-application fees, gateway charges, or bandwidth limitations. It’s simply priced per user. What could be easier?
Your time is valuable. And believe it or not, Banyan can help get you up and running in under 15 minutes. We’re confident that by seeing firsthand how easy it is to deploy, manage, and use, you’ll convince yourself that you want to work with our team.
Sometimes, you want to read what others have to say, like a respected industry analyst. Garrett Bekker, Principal Information Security Research Analyst at 451 Research recently wrote a great blog on “Improving Business Outcomes with Zero Trust” that can help give you some more context about zero trust’s utility.
So. Where do you start your journey? How about I pack a metaphorical lunch for you, and put it in your backpack. Along with a very real collection of great materials to orient you directionally and help remove any speed bumps so that you can not only begin and track your zero trust journey, but have confidence that you’ll arrive at your intended destination in a reasonable amount of time.
Let’s unpack together and see what goodies I’ve put in your bag.
Learn About Banyan
- Zero Trust FAQ
- We’ve all got questions – here’s some answers
- GigaOm Radar Report for Zero Trust Network Access (ZTNA)
- See how a respected analyst firm looks at leading ZTNA offerings
- NIST Cybersecurity White Paper: Planning for a Zero Trust Architecture
- Written for government agencies, this is a valuable resource for the private sector as well
Is Our Platform a Good Fit?
- Chase Cunningham installs Banyan Security video
- See how easy it can be to get a ZTNA solution up and running
- ZTNA Evaluation Guide/Checklist
- How do I compare ZTNA offerings?
- Customer Case Studies
- How are other organizations making use of zero trust network access?
How to Get Started With Banyan
- Banyan Security Team Edition
- Get your zero trust implementation going in 15 minutes for free!
Resources and Reference Material
- Banyan’s Zero Trust Glossary of Terms
- Handy list of frequently seen industry terms from network security, cloud security and zero trust terms
- NIST Special Publication 800-207, Zero Trust Architecture
- Good foundational material walking through why zero trust should be your north star
The above collection is a great starter kit that you can digest on your own as you begin your zero trust journey. Of course, we here at Banyan Security would love to help you, so don’t be shy.
Set up a conversation with a zero trust expert. We want to see you succeed!
About Banyan Security
Pioneering Zero Trust Remote Access
At Banyan Security, we are at the forefront of revolutionizing remote access with our advanced Zero Trust platform. Our platform is specifically designed to provide secure, seamless access to your organization’s resources across the network, including both hybrid and multi-cloud setups. Our platform stands out in the realm of cybersecurity by significantly minimizing the attack surface, effectively obstructing lateral movements, and robustly preventing unauthorized access to critical systems. Our platform’s scalability and effectiveness have made it a trusted choice for enterprises across various sectors, including healthcare, manufacturing, and technology.
Central to Banyan Security’s approach is our groundbreaking TrustScoring system, which is powered by sophisticated machine learning algorithms. This system ensures a comprehensive authentication and authorization process, confirming the credibility of both users and devices. By implementing this, Banyan Security grants access based on the principle of least privilege, ensuring users have just enough access to perform their tasks, thereby safeguarding sensitive corporate applications and servers from potential threats.



