Last year in 2022, there were 1,802 data compromises affecting more than 422 million people – but the LastPass data breach is the one that has security practitioners chatting. The original incident happened in August of 2022. Initially, we were told it was a “minor” breach…yet the story continues to evolve even at the time […]
Blog
Malvertising (the nefarious practice of placing digital ads leading to malware) has been making a resurgence over the past few weeks. For quite a while, cybercriminal gangs have been making fake websites leading to downloads of well-known software that is actually malware in disguise. This latest batch of malvertising, however, is coming from familiar faces […]
Zero trust network access (ZTNA) is becoming increasingly relevant as the concept of the network perimeter, and the traditional “castle-and-moat” mentality of cybersecurity becomes obsolete. The advent of mobile devices, Wi-Fi networks, remote work and work-from-home models, internet-of-things (IoT) devices, cloud computing, SaaS apps, and the increasing diversification of the modern workforce have all contributed […]
The idea of customer self-service has been around since 1833 when Percival Everett’s first self-service vending machines appeared in London, selling postcards. But when it comes to IT, many organizations find self-service daunting (though they agree it can be a path to increasing productivity and profits while reducing costs). Self-service, at its best, allows users […]
Virtual Private Networks (VPN) have been widely used as a solution for secure remote access for decades. However, as organizations have come to rely more fully on remote access as a strategic part of their business, legacy VPNs have been showing their evident shortcomings – significant security weaknesses, inconsistent-to-bad performance, and an often poor end […]
Introduction There’s no escaping the number of breaches occurring daily, our media is full of them. As practitioners it feels like we’re pushing rope uphill as we try to convince organizations to adopt the basic security practices that will help thwart attacks. At the same time we’re fighting for the budget to secure the organization […]
Protecting users against malicious sites and enabling acceptable use policy (AUP) may be accomplished using some basic tools, however, modern organizations don’t have the resources or time to discover, track, and analyze millions of domains. Banyan Security’s Internet Threat Protection (ITP) has some advanced functionality that not only makes this easier but also enhances usability […]
So you’re in charge of your organization’s DNS and hybrid access, and part of the job is providing DNS records to make systems easily accessible but you also need to make sure that you’re preventing spoofed domains, which can lead to a security breach. The first step is to ensure that your workforce is educated […]
What is the VMware ESXi OpenSLP heap-overflow vulnerability (CVE-2021-21974)? A new heap-overflow vulnerability (CVE-2021-21974) has been discovered in the VMware ESXi OpenSLP service. This vulnerability allows attackers to execute arbitrary code and take control of the affected system, posing a serious threat to organizations that use VMware’s ESXi to manage their virtual infrastructure. On February […]
With IPSec, SSL, TLS, VPN, SDP, and ZTNA tunnels, it may sometimes become confusing to figure when to use which. IPSec was mostly used for site-to-site VPN and we’re going to focus on remote access. Clearly, there are different types of tunnels and different ways these tunnels are being configured. With most organizations looking at […]
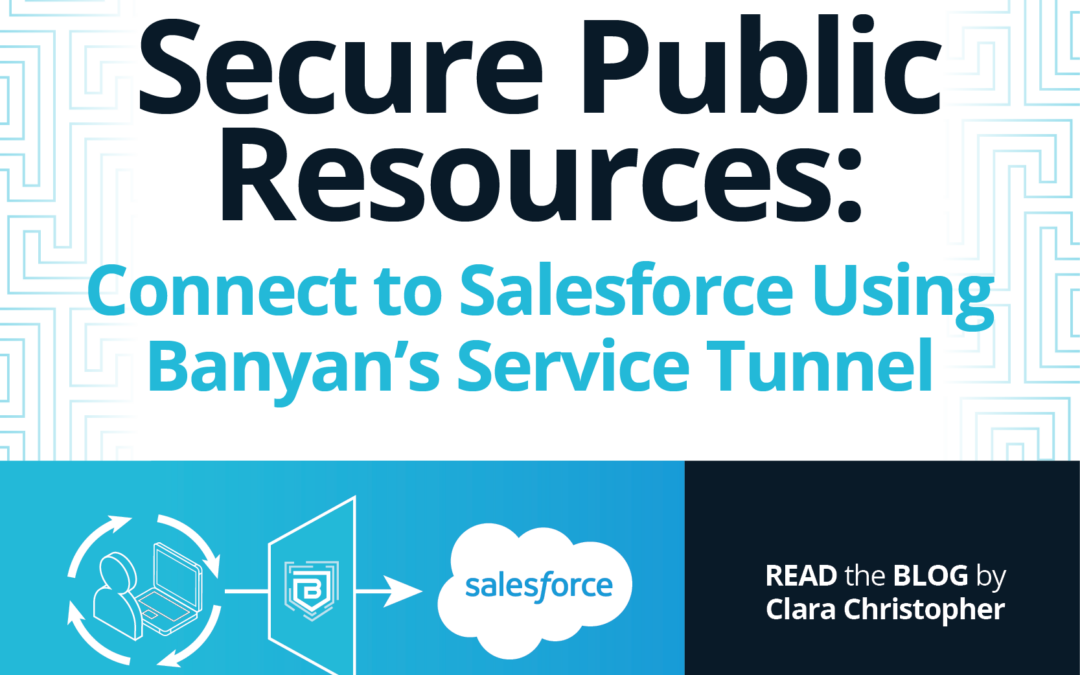
Corporate employees are often required to do work that involves using publicly-accessible resources (e.g., Salesforce or a staging website), which go beyond the bounds of private network control. In light of the need to connect their workforce to these public SaaS applications, many organizations recognize the need for better security, visibility, and flexibility than legacy […]
VPNs, or Virtual Private Networks, have been around for quite some time. But in their legacy form, remote access VPNs are not the safest security solution in this post-COVID, work-from-anywhere, hybrid work environment we live in today. There are key differences between Zero Trust Network Access and traditional VPN that we highlight here, as well […]